This 2026 report, “Beat the Bypass: A Benchmark Study of WAF Weaknesses and AI Mitigation” contextualizes and quantifies why security teams treat Web Application Firewalls (WAFs) as necessary infrastructure, but not as a mitigation layer for critical vulnerabilities, CVEs, or today’s AI threats.
It also addresses a strategic question for modern defense programs: can organizations leverage the WAF’s unique edge position to become an AI-ready, reliable mitigation layer if they augment it with runtime intelligence?
Andy Ellis, former Chief Security Officer of Akamai asserts,
"This study clarifies that WAFs are currently an underutilized asset because the manual, generic signature model erodes trust. Security teams cannot afford the risk of false positives or waiting 41 days for vendors to test CVE-specific rule changes. We see massive untapped potential here: runtime augmentation provides the necessary intelligence and automation to finally transform the WAF into a reliable, high-confidence defense layer for all critical CVEs, not just reactive, one-off fixes”
The study comes on the heels of the discovery of "React2shell" (CVE-2025-55182), a critical vulnerability in React and Next.js. This unfolding crisis serves as a stark, real-world validation of the study’s conclusion: the exposure window between exploit discovery and effective WAF protection is where the damage can happen.
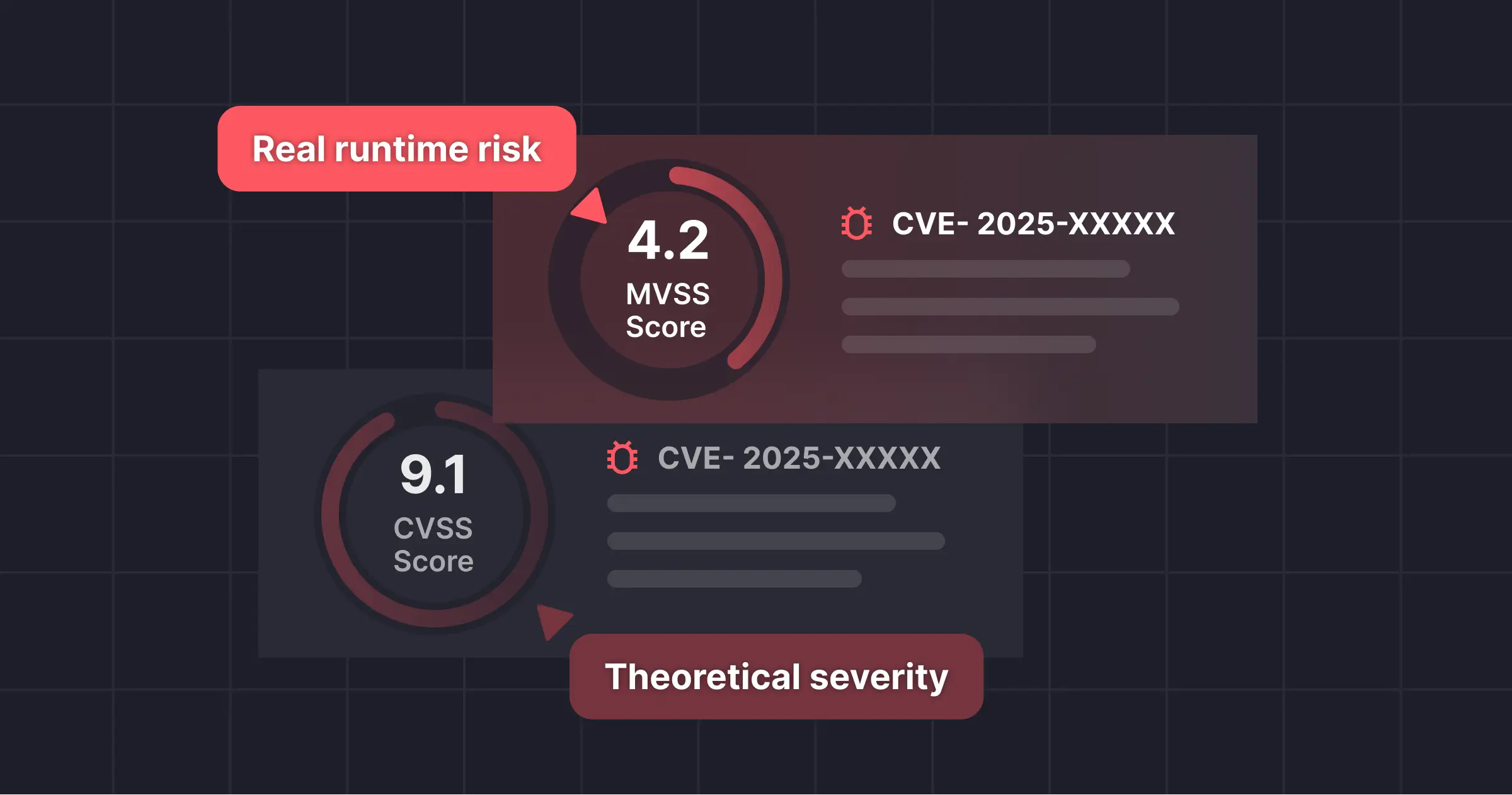
“WAFs are necessary, but they cannot win the AI-enabled zero-day race alone," asserts Daniel Shechter, CEO and Co-founder of Miggo Security. "The 'React2Shell' vulnerabilities are the textbook example of why the old model fails. We have a CVSS 10.0 threat where the exploit lives in the complex deserialization logic of the 'Flight' protocol – a place standard WAF signatures rarely look. The only way to close this 41-day gap is shifting from slow, generic signatures to fast, exploit-aware rules generated by runtime intelligence.”
Miggo’s benchmark study analyzed a representative sample of 360+ CVEs for WAF testing across leading WAF vendors. The curated dataset reflects realistic attacker focus: availability of exploit tooling, prevalence of affected components, and severity of impact – and how AI augmentation can profoundly provide protection:
Key Findings

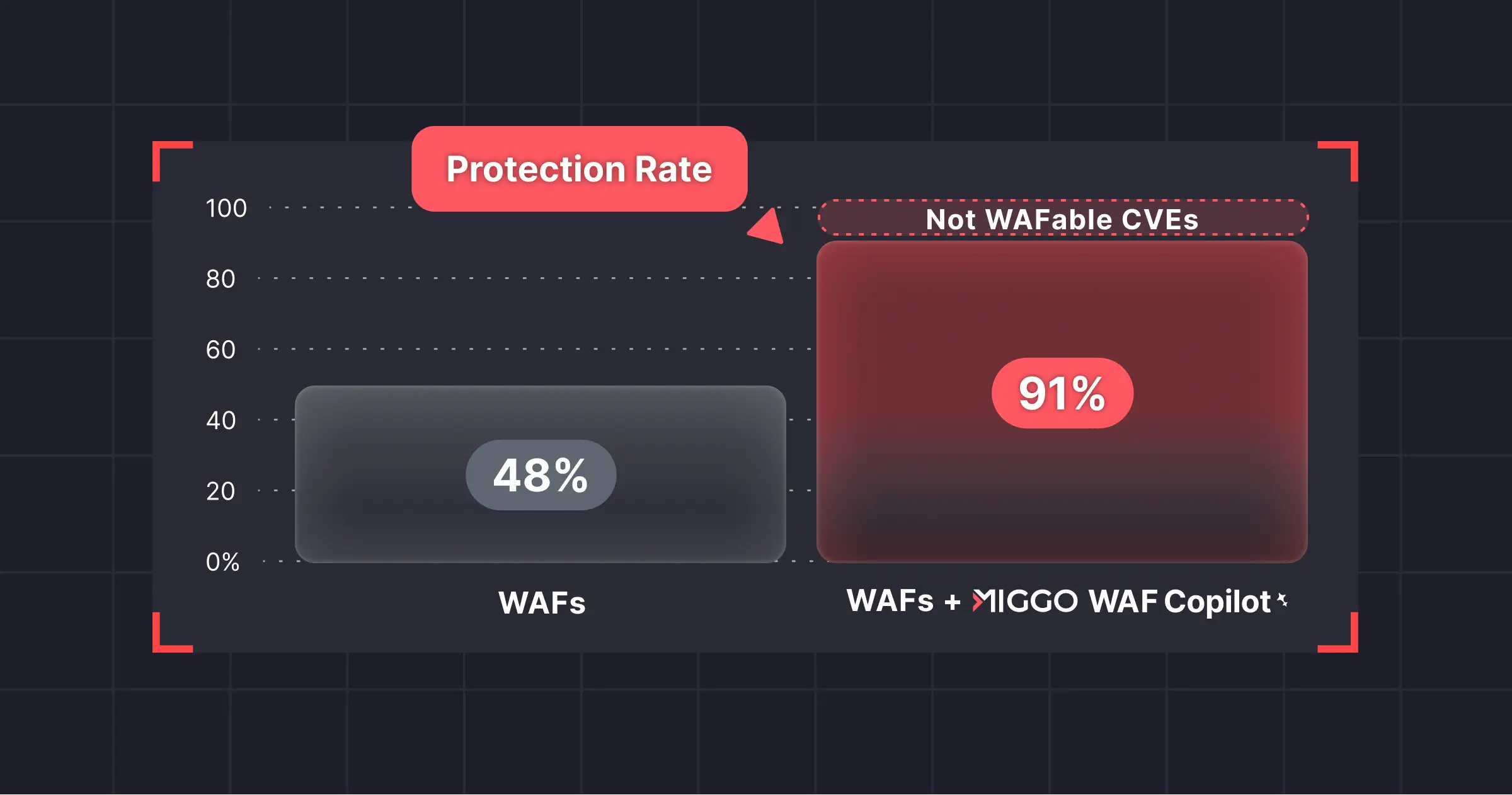
- Most publicly relevant vulnerabilities bypass leading WAFs
52% of exploits bypass default rules even under favorable conditions. Real attacker payloads’ variability only pushes that number higher. - AI-powered tailored rules push coverage above 91%
+90% percent of bypassed vulnerabilities can be mitigated when rules are tailored with AI for the actual vulnerability and application context instead of generic attack patterns - WAF rule releases are 41x slower than AI-native attackers
It takes 41 days on average for a CVE-specific WAF rule to be published by leading WAF vendors, while exploit code appears within hours. This mismatch defines the modern exposure window. - $6 million in potential enterprise losses are estimated due to operational WAF deficiencies, annually for a mid-sized enterprise, because of the exposure window, unnecessary remediation costs, and false positives’ impact. An augmented approach can reduce these significant losses.
Julien Bellanger, former Imperva CMO, Co-founder of RASP pioneer Prevoty and Miggo Security Board member says,
"The data in this report validates the uncomfortable truth we see daily: vulnerabilities are being weaponized faster than any manual process can handle. We know WAFs can be used as a critical mitigating control, cases like Cloudflare's effective initial response to the React2Shell vulnerability prove that. However, the moment a vulnerability is out in the wild, an arms race starts where AI attackers are faster than ever. The imperative now is to make WAFs smarter and more automated so security teams can trust them to reliably implement protection against the 99% of vulnerabilities that do (and don't) make headlines."
The uncomfortable truth is that WAFs, despite being a ubiquitous component of security infrastructure, are failing to serve as a reliable primary mitigation layer.
The $6 Million Question
The cost of WAF inadequacy in today’s AI fight isn't just theoretical risk; it is a tangible line item. The report estimates that the operational inefficiencies of traditional WAFs, spanning emergency remediation, false positive triage, and exposure risk, cost a mid-sized enterprise of over $6.3 million per year.
By shifting from emergency "fire drills" to automated, high-confidence virtual patching, organizations can avoid:
- The massive financial risk of a breach during the 30+ day exposure window.
- $270K in annual direct engineering labor for emergency fixes, and other disruptions to product roadmaps and sprint cycles.
- $100k cost for false-positive chasing
For the full benchmark metrics and cost breakdown, read the full report here.


.png)