On-the-ground update: CVE change clarification
CVE-2025-66478 has officially been marked as a duplicate of CVE-2025-55182. This aligns with the reality that both stem from the same underlying vulnerability. Importantly, this does not imply that detections tied to CVE-2025-66478 are incorrect or false positives. Instead, CVE-2025-55182 now serves as the canonical identifier covering both variants.
Due to the critical nature of these vulnerabilities, exploitation details will not be publicly disclosed in this blog post. Research is ongoing and the blog will be updated with new findings. Access Miggo's live resource page here: https://react2shell.miggo.io/
What Is Going On?
Two critical vulnerabilities have been identified in React Server Components (CVE-2025-55182) and Next.js (CVE-2025-66478). These CVEs enable unauthenticated remote code execution through a prototype pollution attack in the RSC "Flight" protocol's deserialization logic.
No special setup is needed to be vulnerable. The exploitation is unauthenticated (no login required), remote (exploitable over HTTP), and requires no special setup.
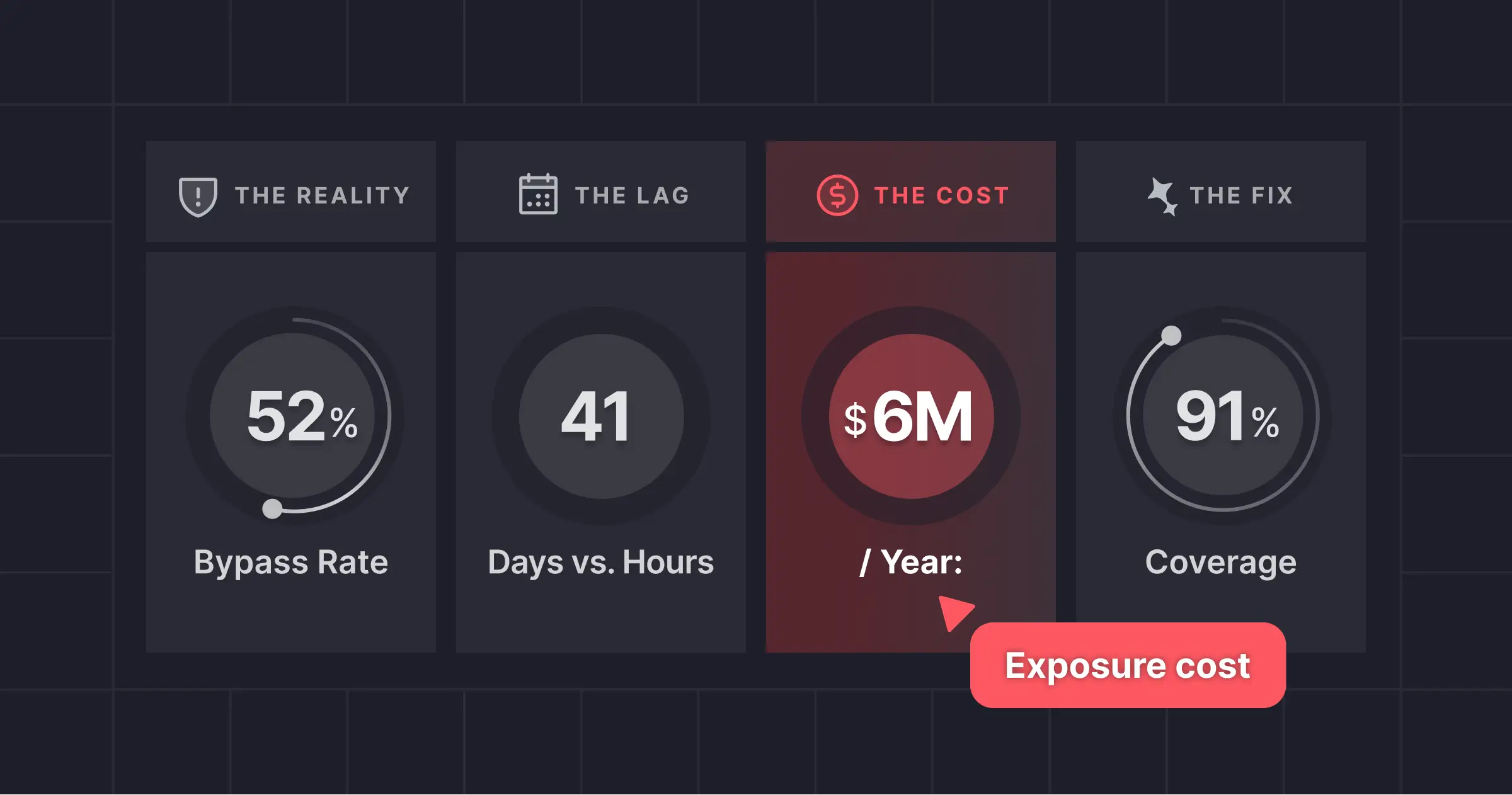
Security researcher Lachlan Davidson reported the vulnerability to Meta on November 29th, 2025. React released patched versions on December 3rd. The vulnerability exists in the default configuration of affected applications, meaning standard deployments are immediately at risk without any special setup required. The scope of affected applications is therefore extremely wide.
What Should You Do?
Immediate Actions
- Patch vulnerable `React` applications:
- Upgrade
reactand any underlyingreact-server-dom-*to 19.0.1, 19.1.2, or 19.2.1
- Upgrade
- Patch vulnerable frameworks that use React as a dependency:
- Upgrade
Next.jsto 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, or 16.0.7 (Use the patch matching your minor version) - Upgrade RSC-enabled frameworks such as
Wakuto 0.27.2,RedwoodJS, to v1.0.0-beta.36, or Vite/Parcel plugins(@vitejs/plugin-rsc)to the latest versions.
- Upgrade
- Deploy WAF rules - Apply the virtual patches above immediately, using custom rules or apply vendor rules (e.g., Cloudflare).
React: A High Value Target with Exceptional Reach
React is the world's most popular frontend framework, and React Server Components (RSC) represent its newest paradigm for building full-stack applications. RSC allows components to run on the server, with a streaming protocol called "Flight" that serializes data between server and client.
This architecture is now the default in:
- Next.js (App Router), powering millions of websites
- React Router, the most popular React routing library
- Emerging frameworks like Waku and RedwoodJS
The concentration of RSC in high-value web applications (e-commerce platforms, SaaS products, financial dashboards) makes this an exceptionally attractive target. Compromising an RSC endpoint gives attackers server-side code execution on applications that often have access to databases, internal APIs, and cloud credentials.
The Vulnerabilities
The root cause lives in React server-side packages (versions 19.0.0, 19.1.0, 19.1.1, 19.2.0):
react-server-dom-webpackreact-server-dom-turbopackreact-server-dom-parcel.
Next.js received its own CVE-2025-66478 because it bundles these packages and is the most widely deployed RSC framework.
Affected frameworks and bundlers:
- Next.js (App Router): 14.3.0-canary.77 and later canary releases, 15.x, 16.x
- React Router: RSC-enabled versions
- Vite RSC Plugin: All versions using vulnerable React
- Parcel RSC Plugin: All versions using vulnerable React
- Waku, RedwoodJS, and other RSC frameworks
We’re Here to Support You
If you identify indicators of compromise or are unable to confirm that your environment is secure, Miggo’s security response team can assist you at no cost. We can help validate exposure, review logs, and provide guidance on next steps. You can reach us by booking time on this link for immediate assistance.




.webp)