In December 2025, the React2Shell crisis (CVE-2025-55182) exposed millions of critical applications, from SaaS dashboards to e-commerce platforms, to immediate compromise. This wasn't just another vulnerability. It was a real-world stress test for one of the most trusted layers in perimeter defense: the Web Application Firewall (WAF).
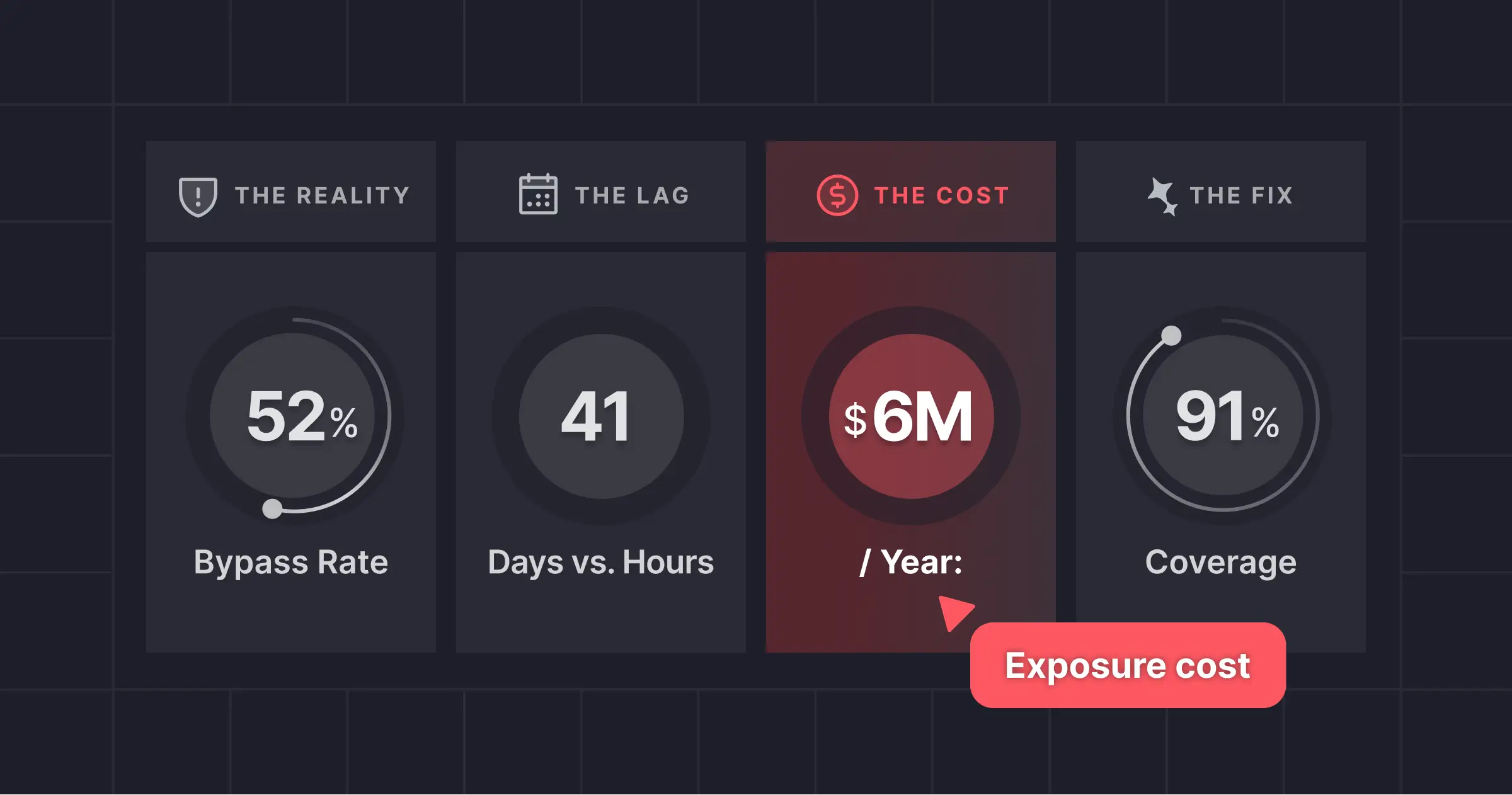
The results of that test are now in, and for many CISOs, they are uncomfortable. In Miggo’s latest benchmark study, Beat the Bypass, we found that default WAF rules fail to block over half (52%) of relevant exploits, even before accounting for attacker evasion techniques. This “Bypass Rate” showed that even when organizations had a WAF deployed, attackers could still bypass it easily.
The data shows that during the early exploit window when it matters most, default WAF defenses fail more often than they succeed, yet they are the ones, if optimized correctly, able to mitigate the attack and keep the organization safe from the CVE exploit.
1. The 52% Reality Check
Traditional WAFs were built for a different era. Today, Miggo's study shows that default WAF rules fail to block over half (52%) of relevant exploits, even before accounting for advanced attacker evasion. Attackers are walking around the front door by simply adjusting request size or structure and techniques perimeter defenses often ignore to avoid breaking application performance. This means a WAF can be deployed, properly configured, and still fail to stop common exploit traffic in the critical first days.
2. The "41-Day" Exposure Window
.webp)
Since AI-led campaigns can weaponize a CVE in minutes, the defense lag is staggering. Attackers weaponize CVEs in hours. It takes the industry an average of 41 days to ship a WAF rule.
- Day 0: CVE disclosed / exploit PoC appears
- Day 1: Attacker scanning, and often exploits, begin
- Day 41: Official WAF rule arrives
This creates a massive exposure window. Attackers don’t wait for patch cycles, they weaponize vulnerabilities immediately as they move orders of magnitude faster than defenders.
3. Quantifying the Business Risk (ROI)
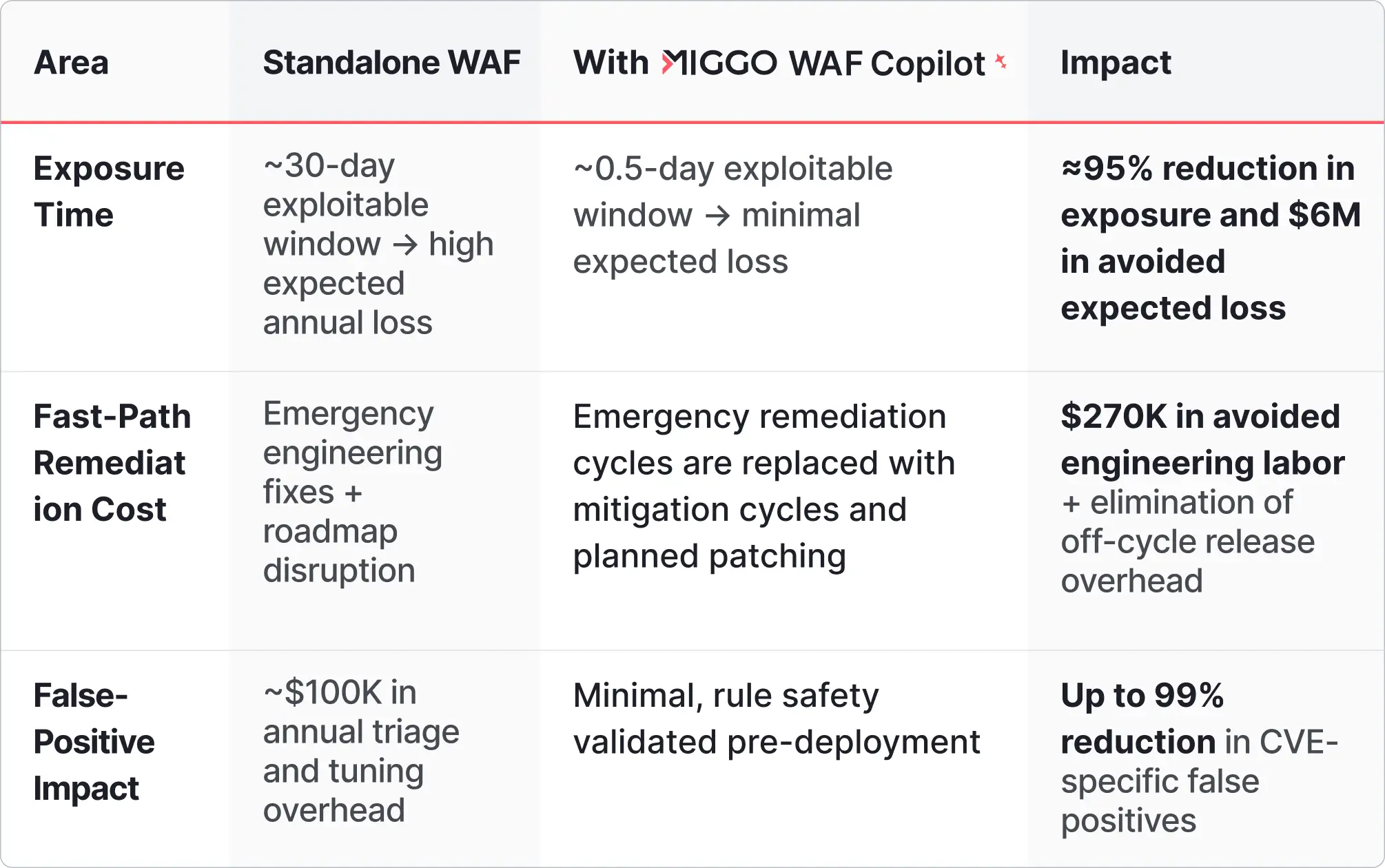
For a mid-sized enterprise, the operational cost of relying on a traditional WAF-led defense is estimated at $6M annually. This includes the cost of exposure, false positives, and remediation. Enhancing WAF with AI, such as through WAF Copilot, delivers a solid ROI by reducing exposure time, cutting labor costs, and nearly eliminating the need for false-positive triage.
- Exposure Time: Traditional patch cycles typically take ~30 days, leading to high expected annual loss. AI-native virtual patching reduces this to 0.5 days, resulting in approximately $6M in avoided annual loss.
- Engineering Labor: Organizations face roughly 30 high-risk, externally reachable CVEs per year. At $9K per emergency fix, AI-driven mitigation can save $270K in avoided direct labor and eliminate off-cycle release overhead.
- False-Positive Triage: Generic WAF rules often cause outages and require roughly $100K in annual triage and tuning overhead. Pre-validated, context-aware rules can reduce this overhead by up to 99%.
4. From Manual Tuning to AI-Native Response
The report highlights a clear shift: Detection is no longer the metric of success; adaptability is. The answer isn’t ripping out your WAF; it’s compressing response time from weeks to minutes. We benchmarked leading WAFs against Miggo’s WAF Copilot to see how AI could bridge the gap.
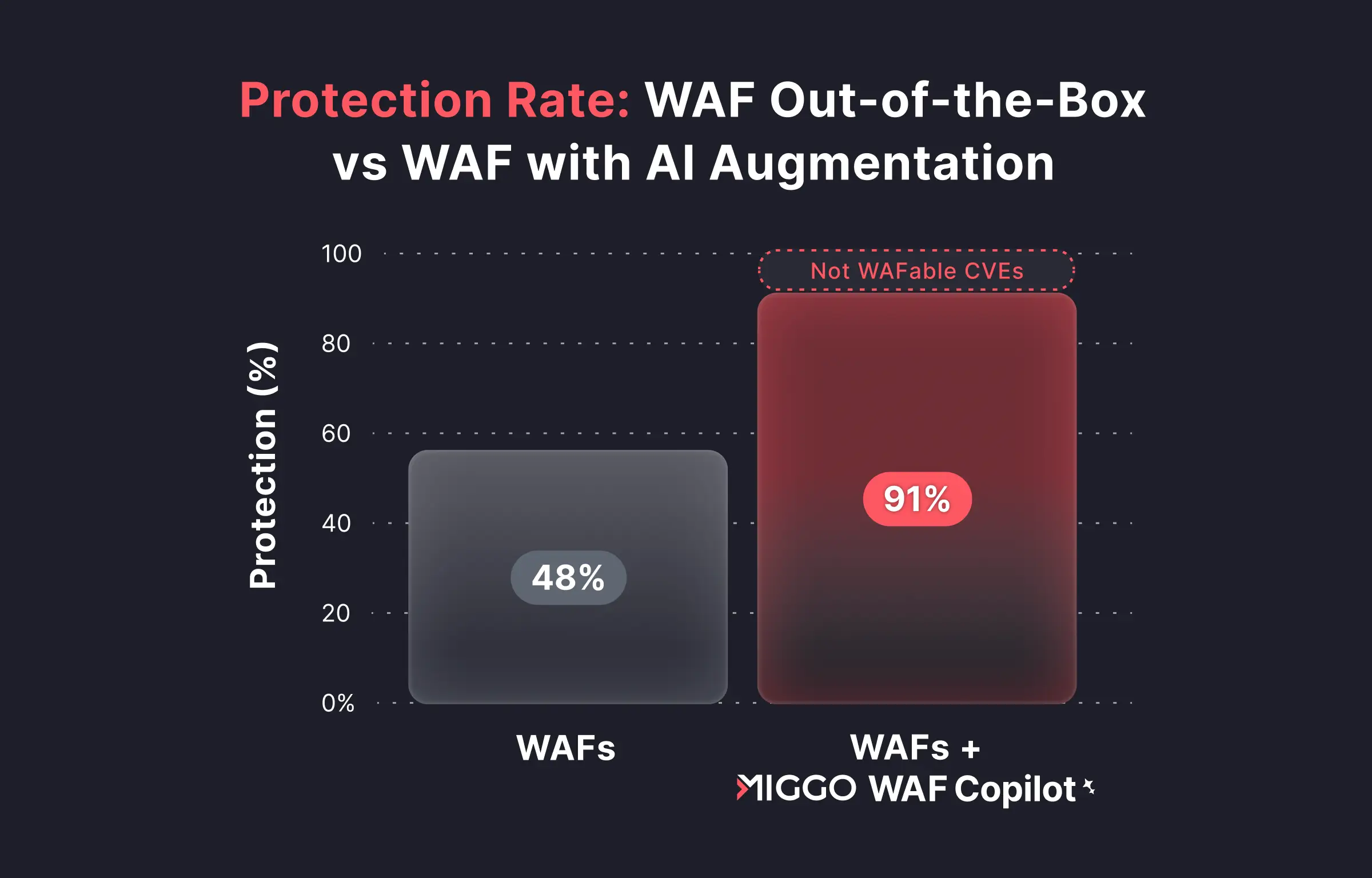
- Context over Generic Signatures: By grounding rules in actual application context and runtime exploitability, coverage jumped from 48% to over 91%.
- Confidence to Block: The #1 reason teams leave WAFs in "Log Only" mode is the fear of breaking production. Automated adversarial testing and application-aware scoping provide the surgical precision needed to move to Block Mode with confidence.
The CISO Imperative: Augmentation, Not Displacement
The conclusion of the 2026 report is simple: You don't need to replace your WAF; you need to give it a brain. Integrating runtime-aware, automated rule generation into the existing stack shifts defense speed from weeks to minutes with a compelling ROI.
As attackers leverage autonomous threats, our defenses must be just as agentic. The window of opportunity is closing—is your WAF still waiting for a rule that’s 40 days late?
Want the full report? Download the 2026 Miggo Benchmark Study here.


.webp)