Beat the Bypass: A Benchmark Study of WAF Weaknesses and AI Mitigation
WAFs were designed for an earlier era of application security. Today, attackers develop exploits within hours, while WAF vendors often take 41 days to release CVE-specific rules. Even in the case like React2Shell, where WAF rules were released within a shorter timespan, bypasses also followed rapidly. The result leads to WAF deployments that block less than half of real-world application-layer exploits, leaving organizations exposed during the highest-risk window.
Miggo’s research benchmarks leading WAF platforms and analyzes how AI-driven rule generation and runtime context can close this critical gap.
This report discusses why WAFs miss modern threats while AI augmentation delivers the paradigm shift security teams need to protect their organization. This AI augmentation, demonstrated by Miggo WAF Copilot uses runtime context, real exploit behavior, and predictive vulnerability modeling to generate protections within hours and scope them precisely to reachable application paths.
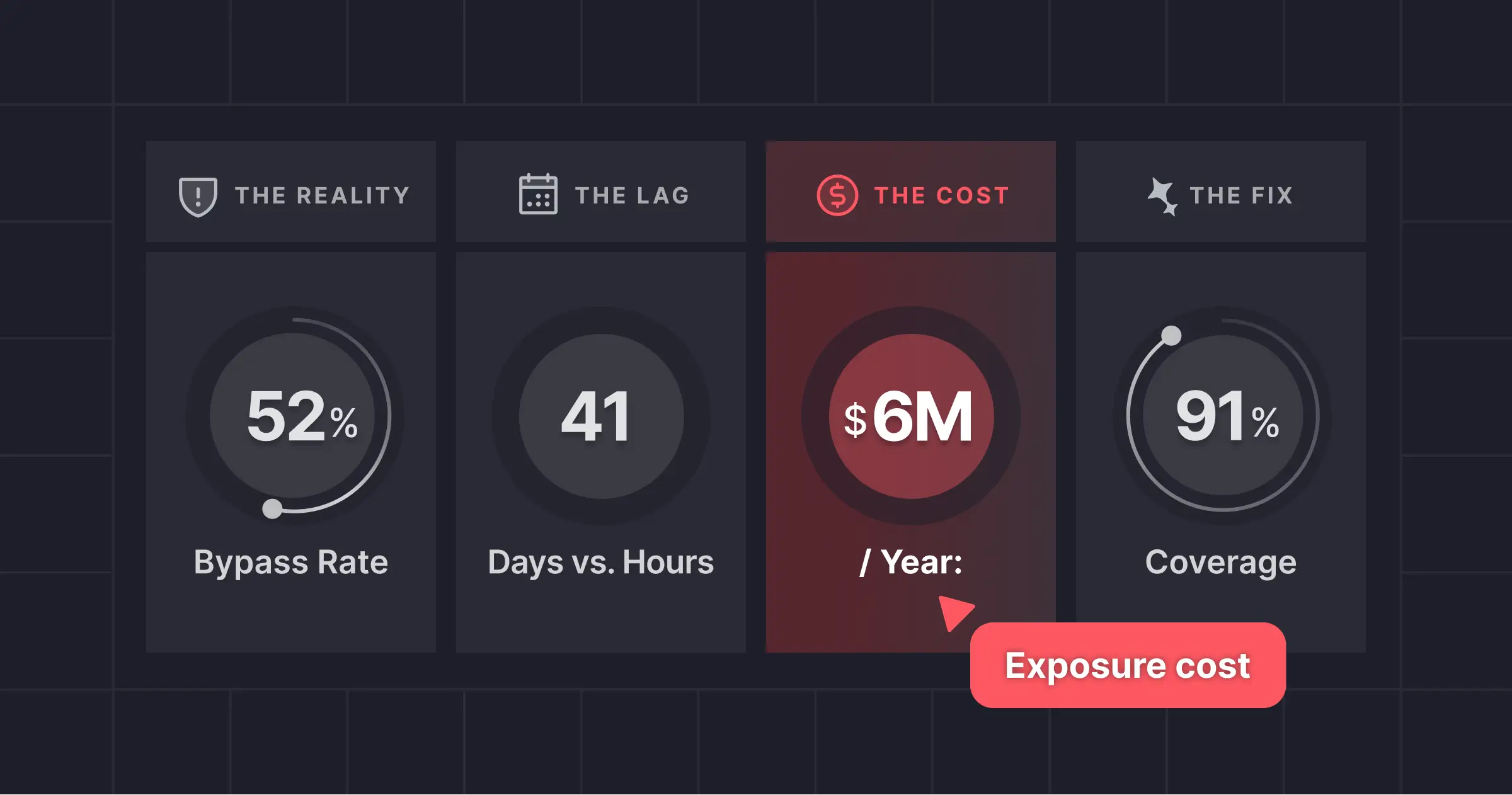
Key Finding: Default WAF rules fail to block 52% of relevant CVE exploits. With AI-tailored rules, coverage increases to ~91%.
What this Benchmark Study Covers
Across more than 360+ CVEs, our benchmark analysis uncovers:
- 48% out-of-the-box mitigation coverage, even for vulnerabilities that should be WAF-mitigable
- 41-day average lag for WAF vendors to publish CVE-specific rules
- $6M per year as the estimated annual cost for a mid-sized enterprise resulting in remediation effort, false positives, and exposure risk.
- Approx 91% of the bypasses are still WAF fixable, showing the gap is about speed and context
For Security Teams Facing These Realities
This report is designed for:
- Security and engineering leaders responsible for application risk
- Teams managing high-volume CVEs and urgent patch cycles
- Organizations relying on WAFs for virtual patching or zero-day mitigation
- Teams seeking real-time, AI-driven protection against fast-moving exploit activity
- Teams struggling with CVEs whose patch cannot easily be fixed or are unpatchable, and need a way to reduce risk
As AI-assisted attackers increase velocity and scale, traditional WAF signatures simply can’t keep pace.
Miggo WAF Copilot’s model-validated rules, runtime context, and exploit-aligned protection, represents a necessary shift in how security teams approach CVE mitigation.
“This approach transforms the WAF into a high-velocity mitigation layer, delivering critical ROI by directly reducing breach risk and minimizing incident response expenditure.”
Download the Full Study
A comprehensive benchmark study covering:
- 360+ CVEs tested across leading WAF vendors
- Bypass patterns and exploit variants unseen by generic signatures
Rule lifecycle challenges and operational bottlenecks - AI-driven mitigation workflows that reduce exposure from weeks to hours
- Full ROI analysis for reducing breach risk, false positives, and emergency remediation costs
Get the full analysis + detailed recommendations for modern runtime defense.
FAQs
What does this study analyze?
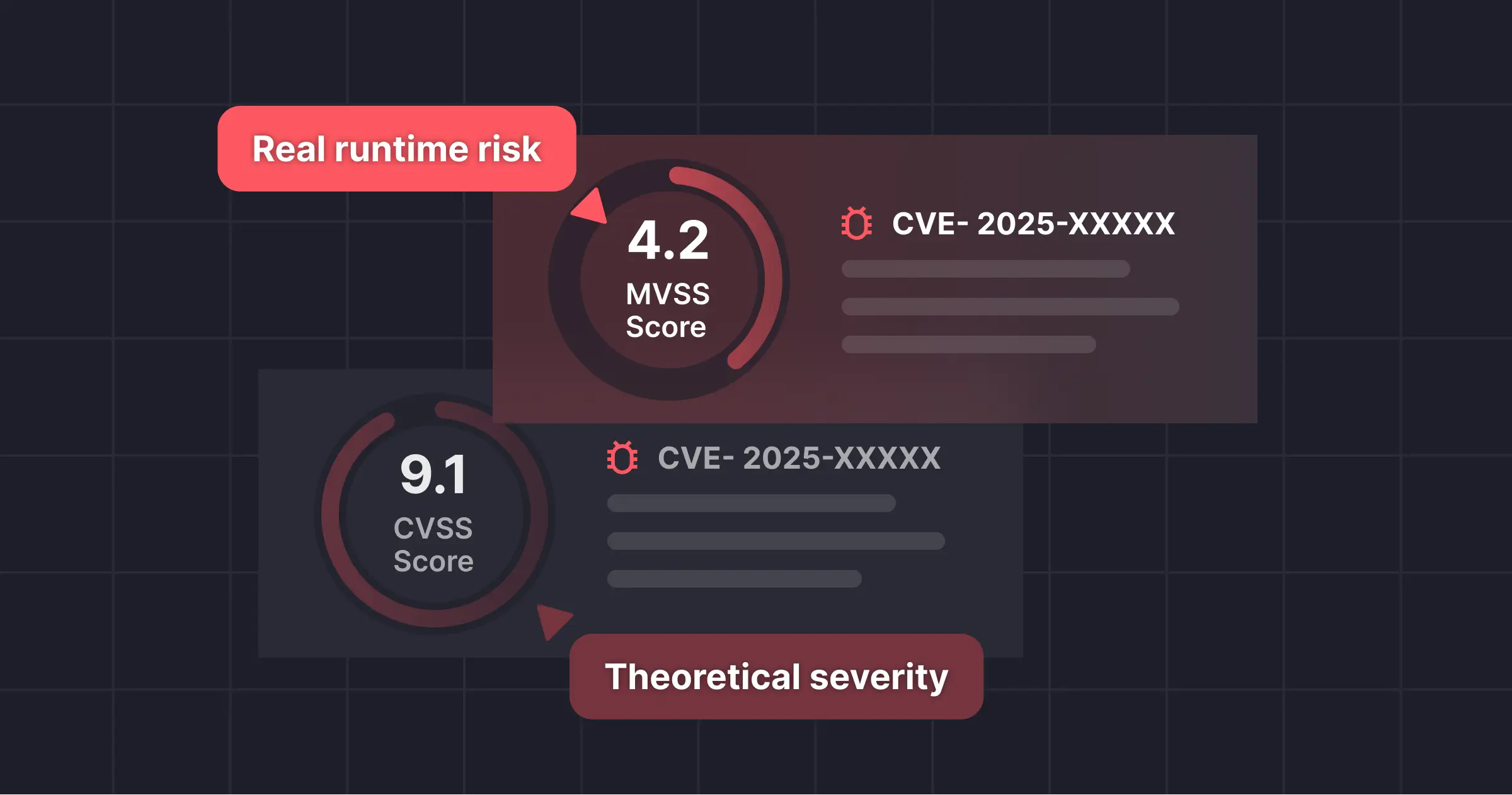
It benchmarks default WAF behavior against modern exploit activity and evaluates how AI-augmented virtual patching improves coverage, speed, and precision.
Why do WAFs miss so many CVE exploits?
Vendors rely on generic signatures and release CVE-specific rules slowly, while attackers generate mutations within hours, often bypassing static detection.
How does AI Augmentation improve CVE mitigation?
It uses runtime context and predictive vulnerability analysis to generate tailored rules for the exact exploit path in your environment, increasing coverage to ~91%.
What is the “exposure window” and why does it matter?
The exposure window is the time between CVE disclosure and effective mitigation. For WAF vendors, it can take up to 41 days to create a rule, and even then it can be bypassed. AI augmentation, like Miggo WAF Copilot reduces it to ~0.5 days.
How is this different from WAF tuning?
AI Augmentation like Miggo WAF Copilot validates rule behavior prior to deployment and applies rules only to endpoints linked to confirmed vulnerable code paths` .
What is the business impact and ROI of AI-augmented WAF mitigation?
AI-augmented WAF mitigation can reduce roughly $270K in emergency engineering work and ~$100K in false-positive overhead, and by shrinking the exposure window from ~30–41 days to ~0.5 days, avoid an estimated $6M in annual breach risk.