TL;DR
CVSS tells you what could matter. MVSS tells you what does matter.
For years, the Common Vulnerability Scoring System (CVSS) has given security teams a shared language to describe the theoretical severity of vulnerabilities. It is a useful baseline. It helps categorize potential impact and provides structure for compliance programs.
But CVSS was built for a different era. It assumes you can understand severity by analyzing a vulnerability in isolation. It evaluates possibility, not exposure. Modern environments don’t work that way. Applications load code dynamically, run across distributed services, and change constantly. Exploits move in hours. Teams handle more vulnerabilities than they can reasonably assess.
Under those conditions, a theoretical severity score provides little direction. It floods teams with “critical” findings that will never matter in practice, while the issues that do put the application at risk slip past the noise. Few things frustrate security teams more than burning time on the wrong problems while real threats stay unchecked.
Enter the Miggo Risk Score
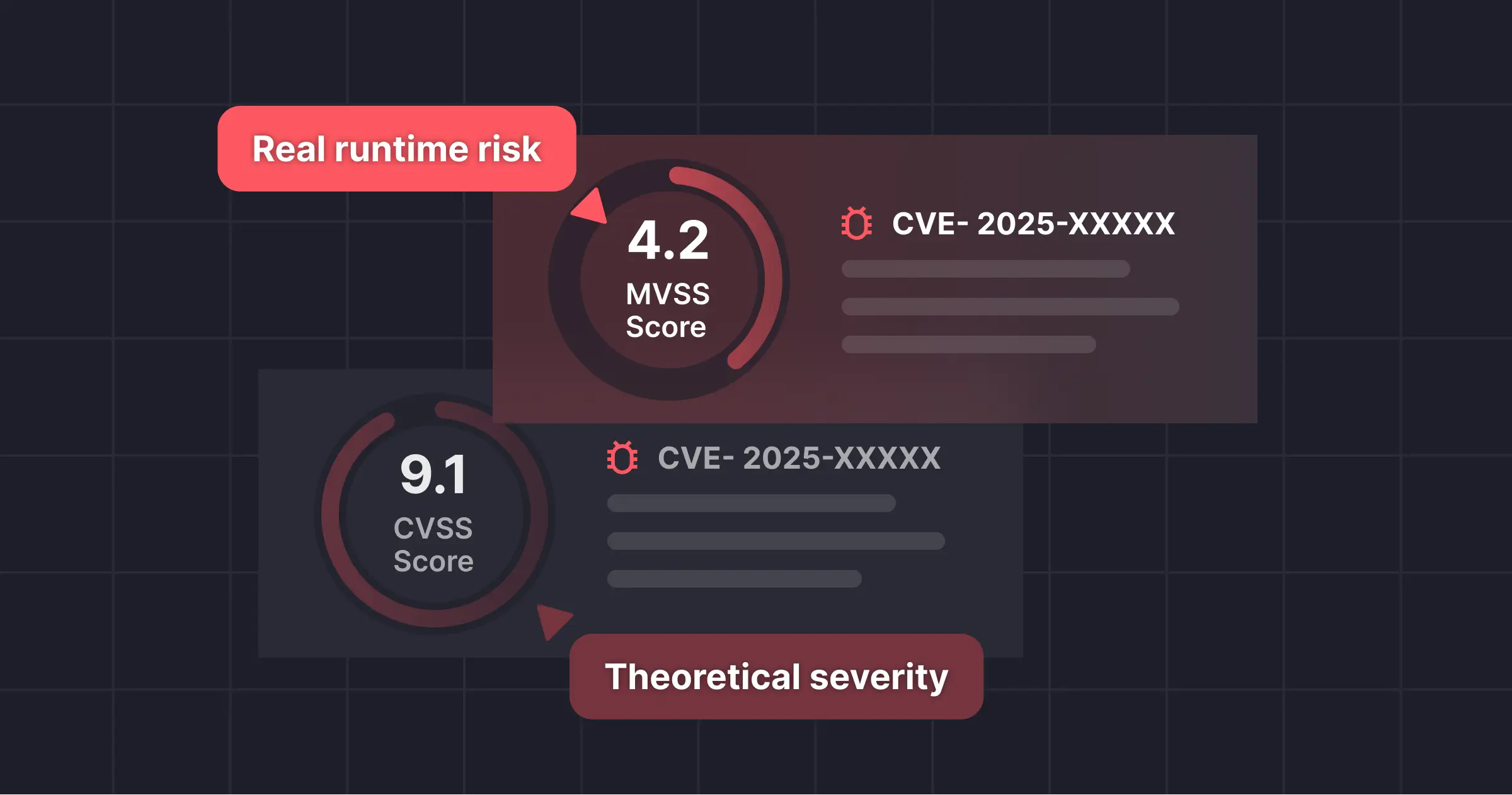
The Miggo Risk Score (MVSS) takes the foundation of CVSS and applies runtime context to determine what actually matters inside an application. CVSS provides the theoretical baseline. MVSS determines whether that severity is expressed in your real environment.
Instead of asking, “What is the potential impact of this vulnerability?” MVSS asks, “How dangerous is this vulnerability to your application right now?”
MVSS focuses security teams on vulnerabilities that are:
- Actually loaded or executed
- Reachable through real traffic paths
- Aligned with exploit conditions present in the environment
This shifts prioritization from hypothetical severity to operational risk.
The best way to understand MVSS is to see it in action. The following walkthrough illustrates how it narrows focus to the vulnerabilities that drive actual risk.
Reducing Noise Through Runtime Awareness
The following chart compares MVSS and CVSS scores for the same set of vulnerabilities. Both scales range from 0 to 10. CVSS assigns many of them scores in the High and Critical range. MVSS compresses those ratings because most of those vulnerabilities are not exploitable when evaluated against runtime evidence.
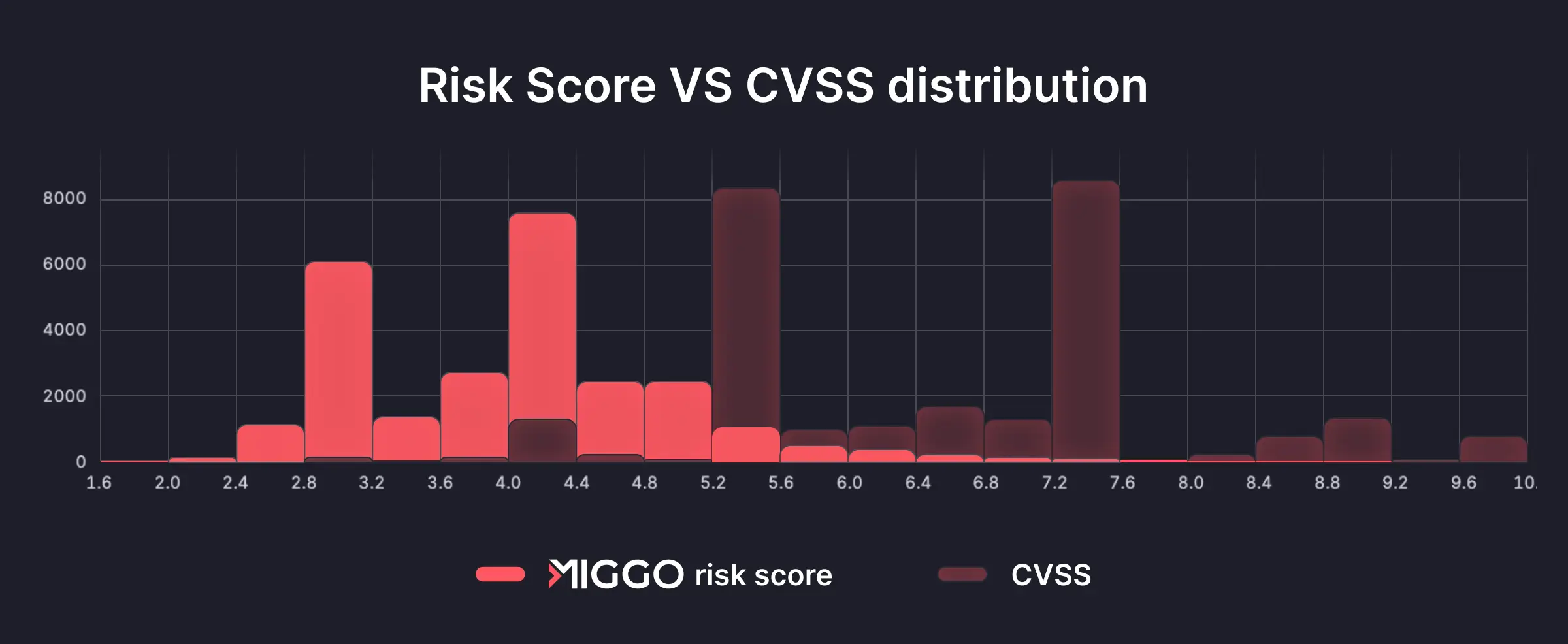
That leftward shift reflects noise caused by CVSS’ theoretical higher severity rankings. Note that CVSS has given a 7.5-10 score to a number of vulnerabilities, indicating that they are critical or high-risk. MVSS reviewed the same vulnerabilities and applied runtime context. It found that those theoretical critical vulnerabilities did not pose a high-severity threat when viewed within a real environment based on an application’s runtime behavior.
MVS compresses the noise and exposes runtime risk for an organization’s specific environment.
Reordering Severity Based on Real Exploitability
The following chart compares CVSS scores (X-axis) with MVSS scores (Y-axis) for the same set of vulnerabilities.
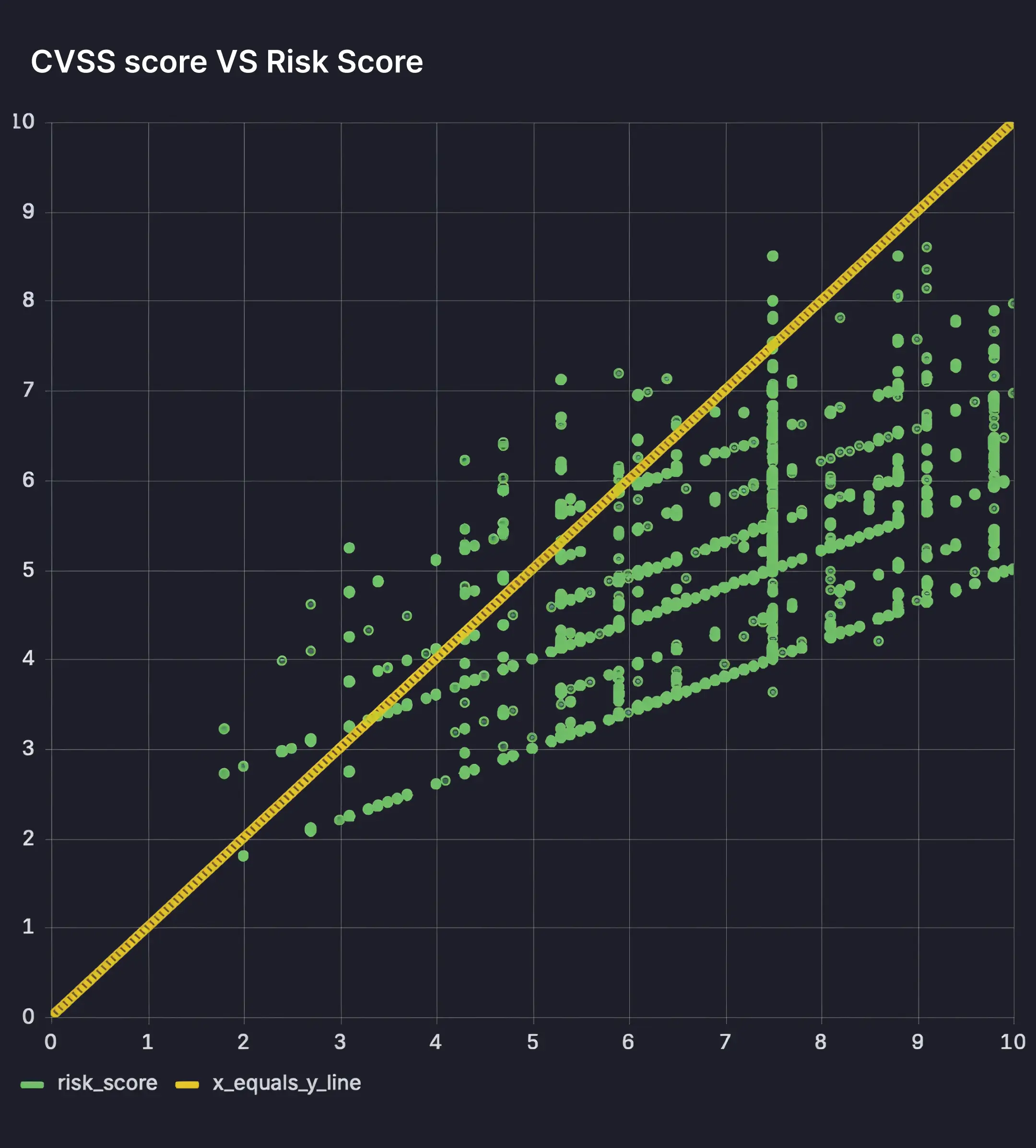
The orange diagonal line represents where both systems assign equal severity, while the green dots represent different severity levels. Most green dots fall below the orange line, demonstrating that MVSS consistently gives lower severity scores because it incorporates and prioritized runtime evidence over theoretical impact.
In practical terms, CVSS scores show a vulnerability that looks severe on paper, but poses a much smaller risk when evaluated in a real environment.
The overall pattern shows MVSS reducing noise by down-ranking vulnerabilities that are less likely to be exploited in practice, allowing security teams to focus their attention on the smaller set of issues that matter.
Ranked Patch List: An AppSec Engineer’s Perspective
AppSec engineers and vulnerability teams typically begin their workflow with a patch list ranked by CVSS severity scores. These theoretical issues drive their attention away from true high-risk vulnerabilities. Replacing CVSS severity rankings with MVSS severity rankings allows them to secure applications that are truly at risk – and allows teams to prioritize and secure applications based on vulnerabilities that are truly at risk in the environment.
We used a dataset of randomly selected vulnerabilities to assess the impact of switching from a CVSS-based priority system to an MVSS-based priority system. Here is what we found out:
- Of the 10 vulnerabilities that received the highest risk score by Miggo (MVSS), none were in the CVSS top 10 rank.
- Looking at the top 50 vulnerabilities ranked by MVSS, the median change in rank (MVSS vs CVSS) was 47, and the average was 101.
The following chart shows how the top 50 CVSS vulnerabilities shift when MVSS is applied to them:
- Left axis: CVSS rank
- Right Axis: MVSS rank
- Each line - one vulnerability’s priority shift
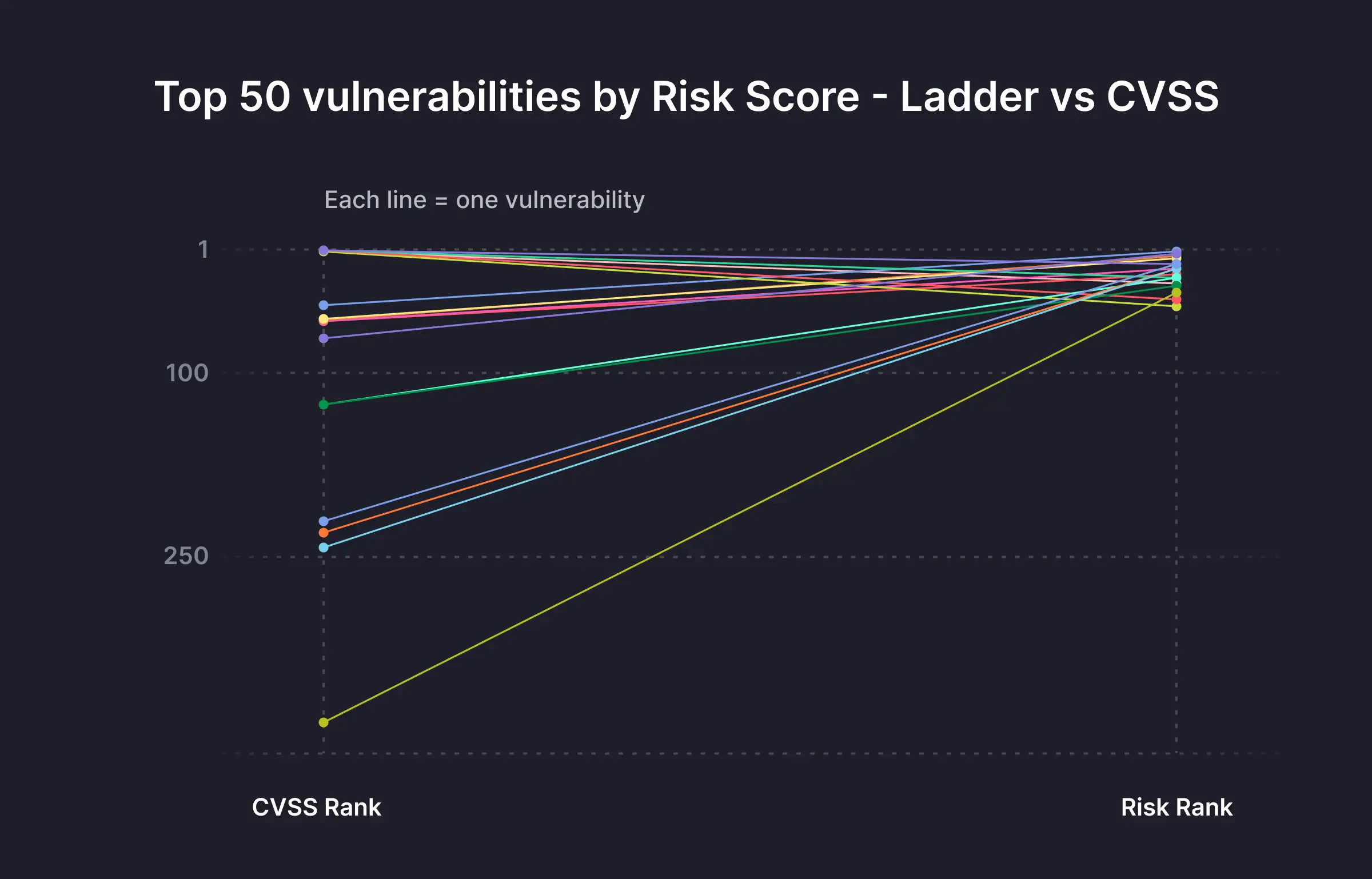
As shown, most of the new top 50 vulnerabilities identified by MVSS started far lower on the CVSS list. MVSS reorders priorities based on runtime evidence, highlighting the difference between theoretical severity and real, environment-specific risk.
Runtime Exploitability & Miggo Risk Score: Where They Apply
MVSS delivers value differently depending on how teams make remediation decisions. The key use cases are as follows:
Risk-Driven Prioritization (Primary use case)
Teams with discretion over remediation need to know what's actually exploitable in their environment, not just what's theoretically severe. MVSS drives prioritization by elevating real exposure and suppressing noise.
Compliance-Driven Patching (Discovery use case)
Teams chasing CVSS metrics don't need risk ranking, as compliance dictates patch order. But if their discovery is weak, runtime visibility finds vulnerabilities scanners miss, ensuring compliance is meaningful.
High-Profile CVE Response (Support use case)
Headline CVEs get patched regardless. MVSS doesn’t drive that decision, but validates urgency or enables quiet deprioritization when a vulnerability isn’t exploitable in the environment.
The Takeaway
CVSS still has value. It remains a useful baseline language for severity and plays a key role in compliance. However, in a world defined by the 4Vs—volume, velocity, variants, and visibility—severity without runtime context becomes noise. MVSS doesn’t replace CVSS as a standard, it complements it with situational truth so teams can:
- Focus on exploitability, not just possibility
- Prioritize what’s reachable, not just what’s rated high
- Reduce risk faster without drowning in “critical” lists
If you want to know how to better identify, map and mitigate threats in your application environment, book time with our security experts.


.png)