With exploit timelines collapsing to near zero, static lists leave security teams exposed and unaware of active threats. In the Missing 88% of Exploits: Rethinking KEV in the AI Era report, Miggo research team breaks down why list-based defense models can’t keep up with AI-driven attackers and how AI Runtime Protection helps organizations evolve from awareness to real-time defense.
Read the full findings and how AI Runtime Protection helps security teams reduce exposure in real time. Download report now.
Or continue for excerpts from the report:
Executive Summary
Modern applications are built on open source code. This approach speeds innovation but expands the attack surface with every imported library and dependency. The result is a growing catalog of vulnerabilities, each one a potential entry point for attackers. Modern exploitation now happens at inhuman, machine speed – finding and exploiting weaknesses the moment they appear. As open source code accelerates innovation, it also multiplies exposure. Every dependency added becomes a potential attack path, and every new disclosure can turn into a working exploit within minutes.
To help organizations focus on verified threats, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) introduced the Known Exploited Vulnerabilities (KEV) catalog in 2021. The KEV list was meant to highlight vulnerabilities that had been confirmed as exploited in the wild.
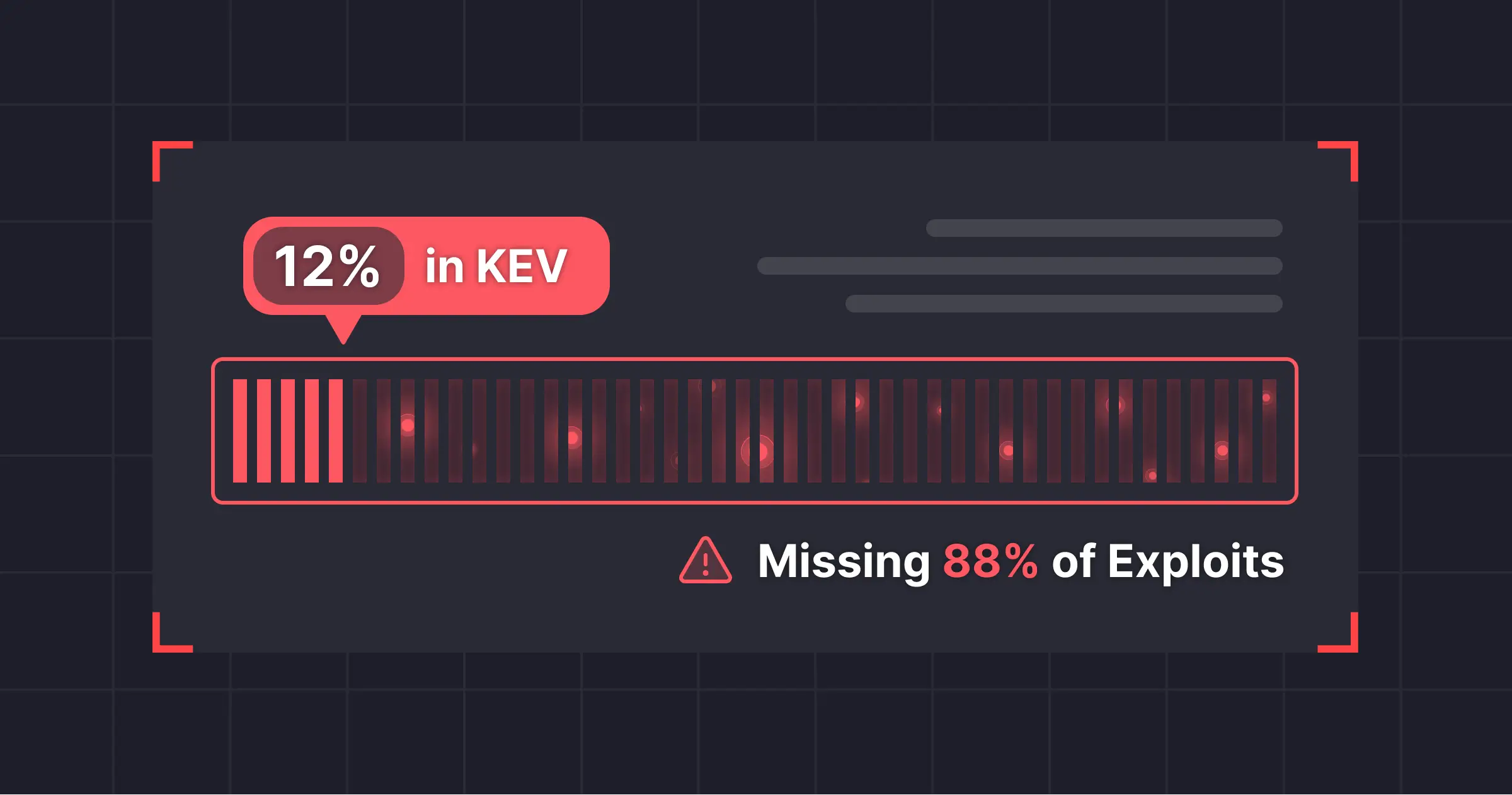
In this study, Miggo Security analyzed over 24,000 vulnerabilities from GitHub’s public open source advisory (GHSA), mapped 572 associated exploits, and compared their presence against the CISA KEV catalog – and found that 88% of CVEs with exploits don’t appear in KEV. While the presence of a public exploit doesn't guarantee that an exploit attempt has occurred, it is a serious indicator of both potential and actual exploit risk. Because KEV focuses on seen exploits against federal and critical infrastructure and relies on vendor specific data sources, it misses a large number of easily exploitable vulnerabilities.
This is the new reality: verification-based defense models cannot keep up with automation-based offense. This paper examines how the KEV catalog functions, how it’s been important for CVE protection programs, and yet, how it struggles to keep up with the speed of modern exploit creation, and what’s missing in the lists. It also takes a look at how defenders embrace runtime context and AI capabilities to overcome the speed and scale needed to react to known and unnamed exploits that are invisible to these static lists.
All About KEV
In November 2021, CISA launched the Known Exploited Vulnerabilities (KEV) catalog, an authoritative list of vulnerabilities that had been exploited in the wild. Using the list, security professionals could easily identify high-risk exposures, and apply patches to those vulnerabilities. It was designed to enable security teams to work smarter, not harder.
KEV adoption within vulnerability management programs gained traction as a trusted reference point for distinguishing between potential and verified threats. Yet despite its value, one major limitation of CISA’s KEV is the delay between when a CVE is first exploited in the wild and when it appears in the CISA KEV catalog. Independent research, including detailed analyses from VulnCheck, has highlighted this timing gap, showing that public evidence of exploitation often surfaces weeks before the affected vulnerabilities are added to CISA KEV.
KEV is a proof-based approach that focuses on confirmed incidents rather than the potential threat of emerging exploits. However, the same reliance on confirmed exploitation that makes KEV authoritative also becomes its constraint, leaving defenders reacting to a subset of exploited CVEs in an environment where new ones can appear at any time.
Falling Behind: The Gap Between KEV and Reality
Miggo Security, leader in AI Runtime Security, maintains an independent Predictive Vulnerability Database (PVD) that continuously aggregates and classifies software vulnerabilities and exploits based on public disclosures across multiple ecosystems.
In this case, based on the proprietary PVD, Miggo’s research team analyzed more than 24,000 open source vulnerabilities drawn from the GitHub Security Advisory (GHSA) database, spanning major ecosystems such as npm, PyPI, Maven, and RubyGems. Within this dataset, the team identified over 1,000 vulnerabilities that included at least one link to a GitHub-hosted exploit repository. The analysis focused exclusively on GHSA advisories to ensure consistency and verifiable sourcing.
Further research found that 407 vulnerabilities contained real exploits and another 165 contained proof-of-concept exploits. These results were compared to the KEV catalog. Despite CISA’s commitment to keep its catalog up to date, only 69 of the 572 exploits Miggo found were also in the KEV catalog.
That means KEV “missed” 88% of real exploits. For organizations relying on these lists, nearly nine out of ten exploits remain invisible. This gap underscores a fundamental limitation of list-based security: it can only defend against what has already been confirmed, not what is actively emerging. And with exploit campaigns launched by attackers armed with sophisticated AI capabilities, this translates into the risk of breach being quite high.
These findings quantify the KEV Gap: the measurable distance between real-world exploitation and what appears in KEV. Even as the lists grow, the window of time between CVE disclosure and exploit availability has collapsed to near zero.
For teams that track every new CVE, simply knowing about KEV vulnerabilities is no longer enough. The sheer number of disclosures, their rapid growth, and the speed of weaponization make it impossible to patch everything. Modern defenses require understanding which vulnerabilities truly matter and shielding those paths from attack.
Miggo Security’s role in this ecosystem is different from that of KEV. Miggo not only proactively identifies vulnerabilities and exploits, it contextualizes and maps their attack path to show if relevant to the organization. Then Miggo goes even a step further by providing mitigating controls so that systems are protected while organizations work to fix the problem, a ‘virtual patch’. By combining runtime visibility, proof of exploitability, and instant shielding, Miggo helps security teams stay ahead of AI-driven threats. Not play catch-up.
In an AI Era, Is the KEV Catalog Still the Holy Grail?
This research shows that the KEV database covers only a small fraction of the potential exploitation activity observed across open source ecosystems. But the bigger question is whether any list can deliver meaningful value in an AI-driven world.
With AI assistance, threat actors can now weaponize new vulnerabilities in minutes. The same models Miggo used to validate exploit code can be used by attackers to create it. Every disclosure carries an implicit risk of instant exploitability.
Patches, which can take time to develop, are inadequate against an onslaught of cyberattacks of this magnitude. As the threat actor’s timeline shrinks to minutes, organizations relying on lists and patch windows still need weeks or months to respond. This gap has effectively collapsed the traditional patching cycle. It is not speculation; it is process automation.
This shift makes one thing clear. Security and appsec teams need systems that act as fast as the attackers, and can detect, interpret, and respond inside the runtime itself not just reactively, but proactively. They need to identify and mitigate threats before the exploitation takes place.
.png)
Proactive Runtime Defense: The Only Security for Applications of the AI Era
If exploits now evolve faster than any list can be updated, security must evolve faster than the exploit. That starts with knowing what’s out there, proving what is truly exploitable, and shielding what matters most in real time. Miggo’s proactive runtime defense model unites predictive vulnerability intelligence, reachability analysis, and AI generated virtual patching. It determines which vulnerabilities pose a real risk and deploys immediate, automated mitigations well before attackers can act. This is proactive security, not just runtime security.
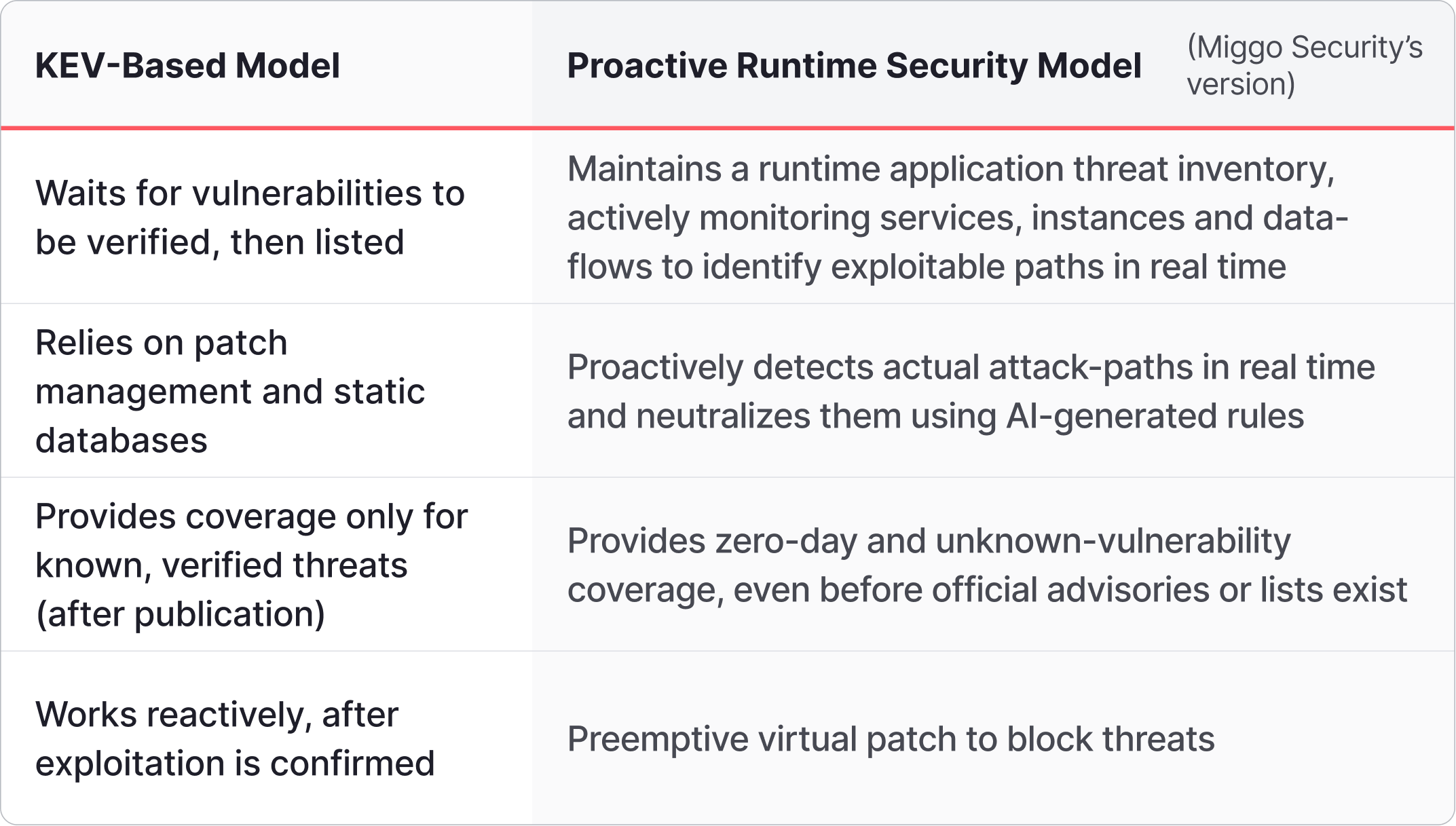
Unlike list-based or patch-driven security models, runtime defense operates continuously inside live applications. It doesn’t wait for published CVEs or external confirmations. Instead, it uses application behavior, data-flow context, and real-time attack-path visibility to spot and stop exploit attempts as they unfold.
Traditional vulnerability management workflows rely on three sequential steps: disclosure → confirmation → patching. In today’s AI-driven landscape this sequence collapses. Runtime defense bypasses the need for external lists by acting at the execution layer, lowering the mean time to mitigation from weeks or months to seconds.
In parallel, Miggo extends this runtime intelligence outward, constantly scanning the global threat landscape for both official and unofficial vulnerabilities and exploits. It automatically triages findings relevant to each customer’s application ecosystem and correlates them with live runtime data to pinpoint risk exposure and recommend precise mitigations.
Here’s how they compare:
Key Advantages of Proactive Runtime Defense
- Immediate mitigation: Runtime systems analyze live behavior and block malicious paths as they occur, reducing mean-time to defense to seconds
- Zero-day coverage: Because the model doesn’t rely on published feeds, it can defend against vulnerabilities that aren’t yet documented
- Reduced patch urgency: While teams still patch, runtime protection buys them time by containing exploitation surface without immediate dependence on patch rollout
- List independence: Defense doesn’t depend on the completeness or timeliness of KEV lists. Instead, it relies on an internal, dynamic threat-inventory and attack-path analysis
Conclusion: From List-Based to Live Defense
KEV began as a tool to simplify risk management, but as the Four Vs accelerate, it can also create a false sense of security. The solution is not another list but a living defense that reacts as fast as attackers do. In the AI era, every disclosed vulnerability can be turned into a working exploit before it ever reaches a list.
Relying on catalogs or patch cycles means staying one step behind attackers. It’s increasingly irrelevant as the distance, noting that it’s in this subset of OSS, between disclosure and an exploit has shrunk so much by LLMs. Proactive runtime protection reverses that equation. It identifies and mitigates vulnerabilities the instant they emerge, combining live runtime context with AI-generated virtual patches. By analyzing code behavior inside the running application, it detects and blocks exploit activity the moment it begins, even if the vulnerability has never been documented or patched. This proactive model shortens time to mitigate to seconds, buying teams time to patch with exploits. AI-Driven Runtime Security provides that speed, turning vulnerability management from a reactive process into a real-time, preemptive defense system.
In a world where open source fuels development, automation fuels exploitation, and AI logic lives within the applications themselves, AI-Driven Runtime Security is the only way to defend applications in today’s AI attack landscape.