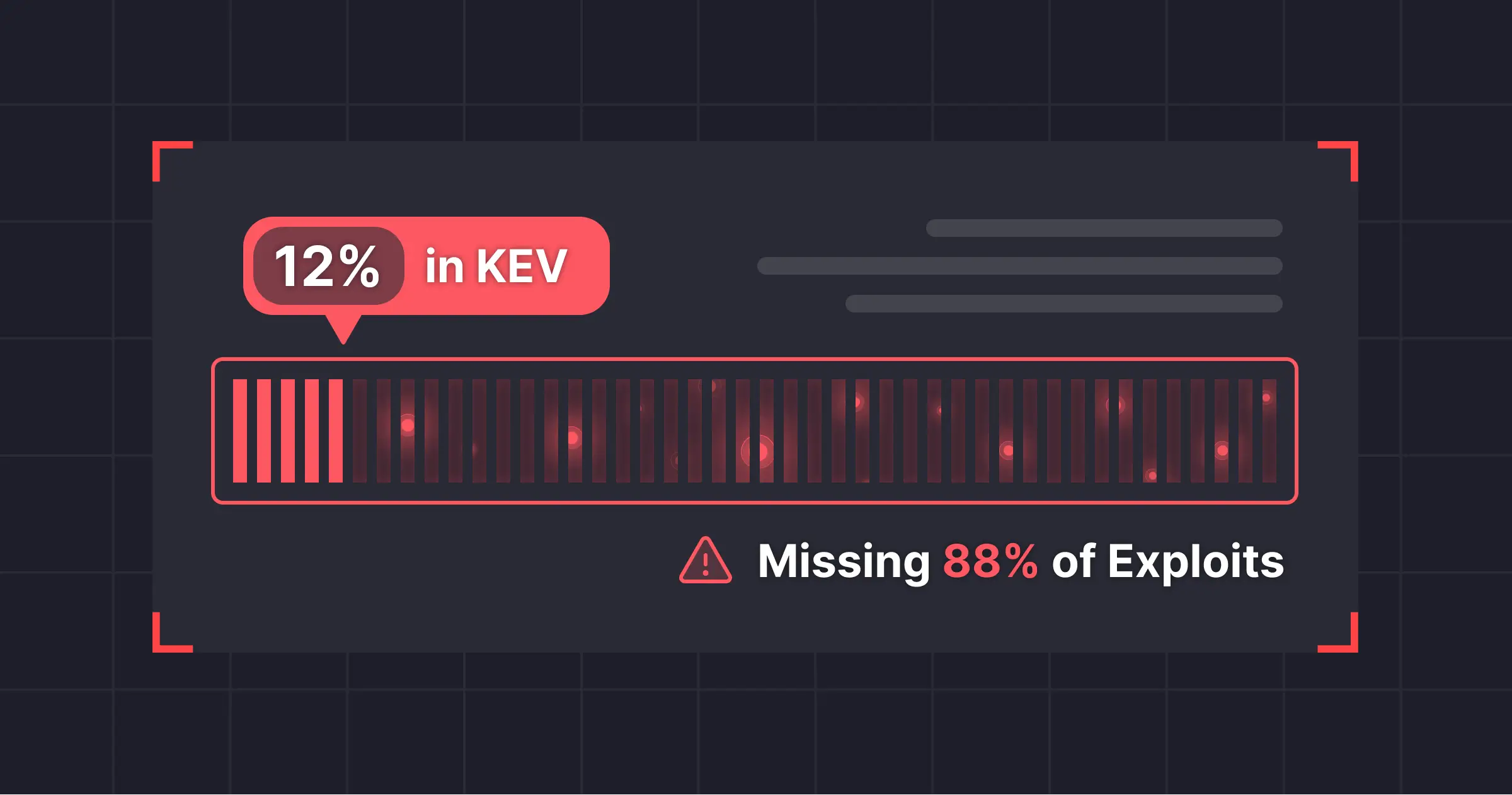
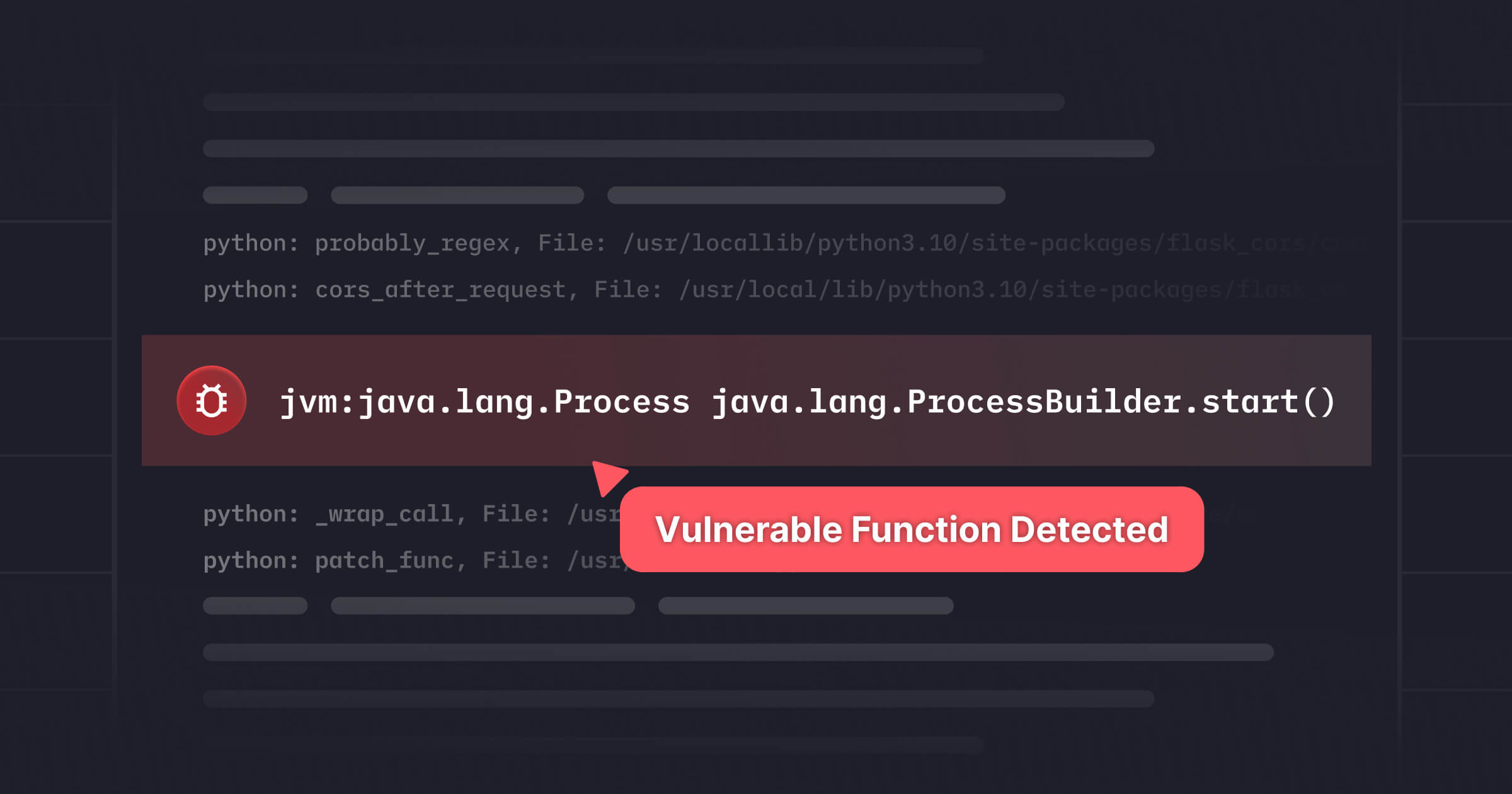
We're excited to announce a first-of-its-kind integration between Miggo's Security Application Detection and Response (ADR) platform and Sentra's Data Security Posture Management (DSPM) solution. This first-of-its-kind ADR-DSPM integration brings together two critical perspectives in application and data security: runtime behavior and data sensitivity. By combining Miggo's runtime application DNA mapping with Sentra's data classification capabilities, security teams can now make decisions and proactively secure critical data with complete business context in a single, unified view and experience improved data security posture.
This partnership represents more than technical integration—it's a philosophy shift in how we approach security. Today, security teams struggle to prioritize effectively while business stakeholders can't grasp true risk exposure, and critical vulnerabilities affecting sensitive data may go unaddressed while teams chase lower-priority issues.
Miggo's ADR platform collects and correlates all databases and tables analyzed by Sentra's DSPM solution with runtime application access patterns, providing unprecedented visibility into the relationship between application behavior and data sensitivity. This unified ADR-DSPM approach ensures that security decisions and actions always happen with full business context.

Dive into the Challenge: Security in Isolation
Typically, application security professionals focus on vulnerabilities and runtime behaviors while data security teams concentrate on classifying and protecting sensitive information. Product security engineers juggle between multiple tools, trying to piece together a coherent picture of actual business risk.
This fragmentation creates critical blind spots. A vulnerability in an application might seem routine—until you realize that application has access to millions of customer records containing PII. Conversely, data security teams might flag sensitive databases without understanding which applications actively access them or how exposed those applications are.
The result? Security teams struggle to prioritize effectively, business stakeholders can't grasp true risk exposure, and critical vulnerabilities affecting sensitive data may go unaddressed while teams chase lower-priority issues.
Consider this scenario: A new critical CVE is discovered affecting a microservice in your environment. Traditional approaches would require:
- Application security team identifies the vulnerable service
- Manual investigation to determine which databases the service accesses
- Coordination with data security team to classify data sensitivity
- Multiple meetings to assess business impact
- Finally, prioritization and remediation
With Miggo's ADR and Sentra's DSPM working together, this entire process happens automatically and instantaneously. The moment the CVE is detected, you know:
- Which sensitive data types are at risk
- The potential blast radius of a compromise
- The business impact in clear, contextual terms
- The appropriate priority level based on actual risk, not assumptions
The Solution: Unified Runtime and Data Intelligence
The Miggo-Sentra integration represents the first ADR-DSPM collaboration in the market, eliminating security silos by enriching runtime application behavior with real-time data sensitivity context. Here's what this means in practice:
Complete Risk Visibility: When Miggo's ADR platform maps your application's runtime DNA, it now automatically incorporates Sentra's DSPM data classification insights. Security teams instantly see not just that a service communicates with a database, but whether that database contains customer PII, financial records, intellectual property, or other sensitive data.
Intelligent Prioritization: An exposed API endpoint is concerning. An exposed API endpoint with access to customer payment information is critical. This integration surfaces these distinctions automatically, enabling teams to focus on what matters most to the business.
Streamlined Workflows: No more switching between platforms, correlating spreadsheets, or holding cross-team meetings just to understand the scope of a security issue. Product and application security teams get the full picture in one place, accelerating response times and reducing mean time to remediation.
Improved Posture: Security and privacy teams gain greater confidence their sensitive data remains secure and compliant no matter where it travels. This enables proactive measures to improve data hygiene by better policy and access controls enforcement - reducing risks before they become something worse.
The Path Forward: Integrated Security for Modern Applications
As applications become more distributed and data more valuable, the artificial boundaries between different security domains become increasingly problematic. The future belongs to integrated solutions that provide complete context and enable intelligent, risk-based decision making and action.
Book your demo now to learn how to proactively secure critical data with complete business context.