We've watched this dynamic unfold across numerous customer environments. The traditional "assess, test, patch, deploy" cycle that once provided adequate protection now feels like bringing a snail to a dog race. When attackers can go from CVE disclosure to working exploits in hours (AI automation ftw), waiting days or weeks for proper patching isn't just inefficient—it's dangerous.
.webp)
Our goal with Miggo WAF Copilot is simple: fundamentally change the timeline of vulnerability response. Miggo takes on the rapid-response, high-volume analysis, so security teams, experts and non-specialists alike, can focus on other high priorities.
Why WAF Automation Is Hard
Automating WAF rules sounds simple. It isn’t.
Step 0: Become aware of the new threat.
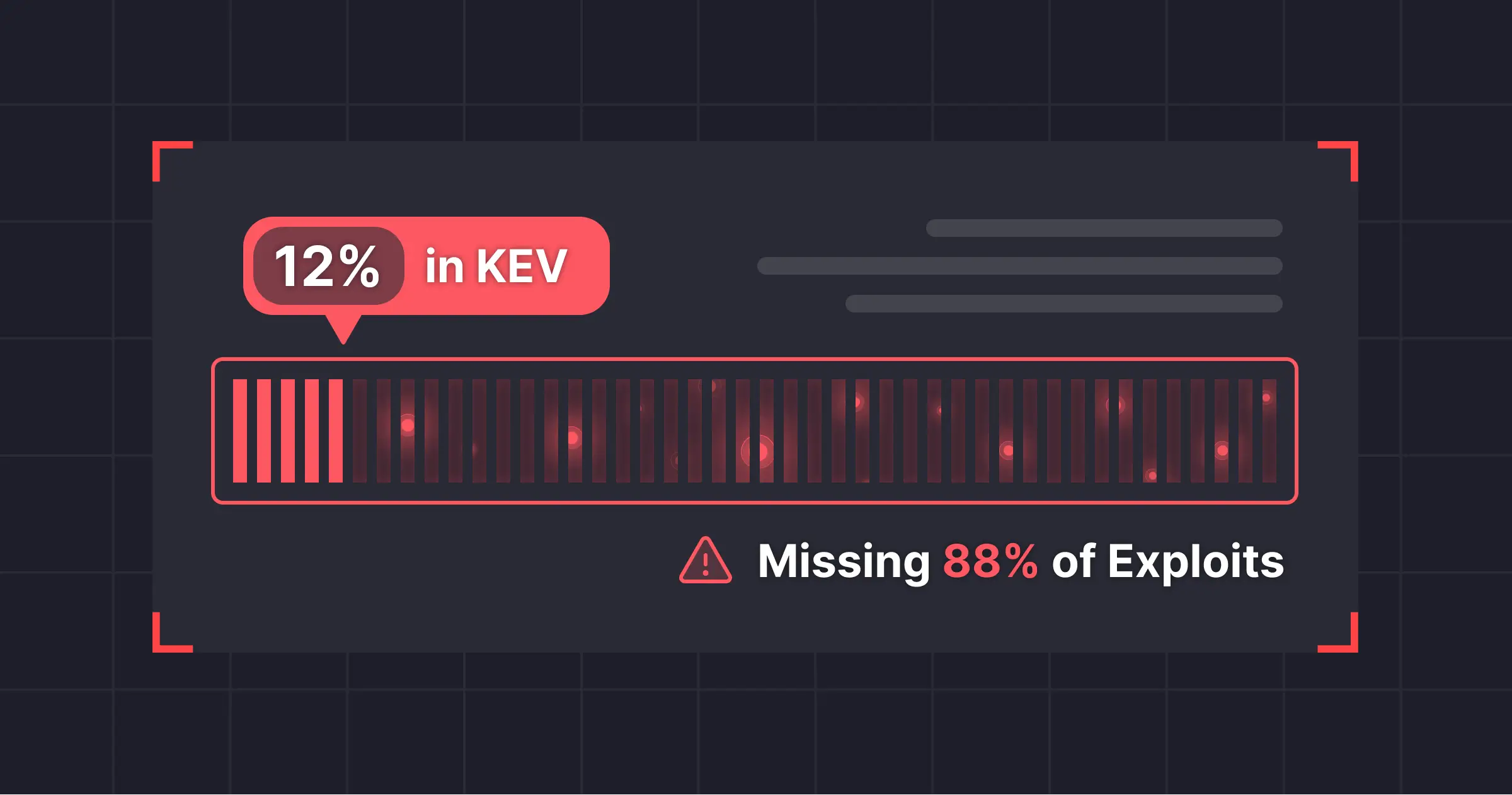
If you don’t see the CVE disclosure, PoC exploit, or vendor bulletin immediately, you’re already behind. Meanwhile? Threat actors are scraping feeds and sharing payloads in private channels within minutes.
Once you become aware, the grind begins:
- Analyze the vulnerability and figure out if your app is actually exposed
- Write and test a rule in your WAF vendor’s syntax
- Hope it doesn’t break legitimate traffic
That process takes hours (sometimes days) and it fails in three predictable ways:
- Generic rules block too much, causing false positives and frustrated, overburdened teams
- Overly narrow rules miss real attacks
- Manual deployment is slow and error-prone, especially across multiple WAF platforms
By the time a handcrafted rule is written, validated, and deployed, attackers have already moved on to the next exploit.
How It Works: Three Pillars of Intelligent Protection
Miggo WAF Copilot operates on three core principles that address the real-world constraints security teams face every day.
.png)
1. Intelligent WAF Rule Generation: Beyond Generic Protection
When a new CVE hits public advisories, Miggo WAF Copilot doesn't just create another generic WAF rule. Instead, it orchestrates a sophisticated analysis pipeline:
Deep Vulnerability Analysis: Parsing CVE disclosures, GitHub security advisories, and vendor documentation to understand not just what the vulnerability is, but how it can be exploited. Miggo Miggo WAF Copilotidentifies attack vectors, analyzes code changes, and maps exploitation patterns with a precision that would take human analysts days to achieve.
Exploit Intelligence Integration: The system continuously monitors known exploits and proof-of-concept code as they emerge, refining protection logic in real-time. When a researcher publishes a working exploit on GitHub, Miggo WAF Copilot immediately analyzes the attack pattern and updates the corresponding WAF rules.
Platform-Specific Validation: Here's where most solutions fail—they generate rules that look good on paper but don't work in practice. Miggo WAF Copilot validates every generated rule against target WAF systems (Cloudflare, AWS WAF, etc.), ensuring syntactic correctness and functional effectiveness before deployment.
2. Application Context Alignment: Surgical Protection, Not Carpet Bombing
Generic WAF rules are the security equivalent of prescribing the same medication for every patient. They might work, but they also might cause more problems than they solve. Miggo WAF Copilot takes a surgical approach:
Exposure Assessment: The system analyzes your specific application architecture to determine actual exposure to each CVE. Not every vulnerability affects every application in the same way. Miggo WAF Copilot understands these nuances, assessing whether a vulnerability is reachable in your environment and what data it might expose.
Attack Path Mapping: Beyond simple vulnerability scanning, Miggo WAF Copilot maps potential attack paths through your applications. It understands how an attacker might chain together seemingly minor issues to achieve significant impact, focusing protection where it matters most.
Context-Aware Rule Deployment: Miggo WAF Copilot doesn't just generate a rule—it determines exactly where and how that rule should be deployed within your WAF setup. It considers your existing rule sets, understands your traffic patterns, and recommends deployment strategies that minimize business impact while maximizing protection.
3. Operationalized Security: Protection You Can Actually Manage
The best security control is worthless if it's impossible to manage in production. Miggo WAF Copilot was designed from the ground up with operational realities in mind:
Business Continuity Monitoring: Once deployed, the platform provides comprehensive monitoring of rule behavior to ensure business continuity. You can analyze logged or blocked requests, identify patterns in legitimate traffic, and receive recommendations for rule refinement. If a rule starts blocking legitimate users, you'll know immediately.
Staged Deployment Strategy: Following security best practices, the system recommends starting with surgical rule deployment in log mode. This allows you to observe potential impacts on legitimate traffic before switching to active blocking, reducing the risk of business disruption.
Flexible Mode Management: Sometimes you need to quickly switch from logging to blocking (or vice versa) based on threat intelligence or business requirements. WAF Copilot provides one-click mode switching with clear impact assessments, so you're never flying blind.
Detailed Impact Analysis: Every rule comes with comprehensive analysis of its effectiveness, including metrics on logged or blocked attempts, and any legitimate traffic affected. This data helps security teams make informed decisions about permanent fixes and long-term protection strategies.
Automated Deployment: For teams ready to embrace full automation, Miggo WAF Copilot can deploy rules automatically through your existing DevSecOps processes, ensuring consistent and rapid protection across your entire application portfolio.
Real-World Impact: What This Means for Your Security Program
The transformation this represents goes beyond faster response times. It's about fundamentally changing how security teams operate in an AI-accelerated threat landscape.
For Security Engineers: Instead of spending hours manually analyzing CVEs and crafting WAF rules, you're reviewing AI-generated protections and focusing on strategic security improvements. The tedious, time-sensitive work is automated, while human expertise is applied where it has the most impact.
For Application Security and Product Security Teams: You gain the ability to provide immediate protection for applications without disrupting development workflows. Developers can continue with proper testing and deployment cycles while security provides real-time protection against emerging threats.
For CISOs: You get measurable reduction in exposure windows and clear metrics on protection effectiveness. When board members ask about your organization's response to the latest critical vulnerability, you can show automated protection deployed within minutes rather than patches scheduled for next week.
For SOC team: By automatically generating, validating in log mode, deploying, and retiring context-aware, precision WAF rules that plug into existing WAF infrastructure, it resolves the challenges of false positives, patching delays, and operational overhead that SOC teams routinely struggle with.
The Bigger Picture: Looking Forward to the Evolution of AI-Driven Security
Miggo WAF Copilot represents a maturation of AI in cybersecurity. Early AI security tools often produced more noise than value, generating alerts that human analysts had to painstakingly sort through.
Miggo WAF Copilot represents the beginning of a broader transformation in how we approach live application security. As AI capabilities advance and threat landscapes evolve, we're already working on expanded capabilities:
- Broader security question capabilities that go beyond CVE analysis to comprehensive security guidance
- Enhanced context awareness that integrates with your existing security tools and processes
- Predictive threat protection that identifies and mitigates attack patterns before they're formally disclosed
Interested in learning more about Miggo WAF Copilot? Contact our team to schedule a demo and see how AI-powered mitigation can transform your security operations.