The Industry's False Choice: Overwhelming Noise vs. Dangerous Blindness
Picture this: It's Monday morning, and your security dashboard shows 3,847 new vulnerability alerts from the weekend. Your developers are already drowning in technical debt, and now they're asking the same question they ask every week: "Which of these actually matter?"
Traditional security tools force teams into an impossible position. Static scanners flood you with "potentially vulnerable" alerts based purely on version matching, while runtime tools promise better context but still leave the critical question unanswered: Is this vulnerability actually exploitable in my specific application?
Most security teams end up making a dangerous compromise - either burning out developers by investigating everything or ignoring most findings and hoping for the best. Neither approach actually makes you more secure.
An objective, evidence-first approach eliminates this false choice: instead of merely detecting vulnerable code, confirm exploitability by tracing execution down to the individual CVE-implicated function in your production environment.
From Reachability to Proof of Execution
While traditional tools stop at detection and behavioral analysis makes educated guesses, an evidence-first approach provides forensic-grade confirmation of exploitability through a four-tier code-path validation framework - and pairs it with internet reachability analysis:
Static → Package exists in container/codebase
Where traditional scanners stop - thousands of theoretical alerts
Loaded → Package loaded into application memory
First runtime filter - eliminates unused bundled packages
Executed → Functions from vulnerable package invoked in production
Where most runtime tools stop - shows package usage but not vulnerability risk
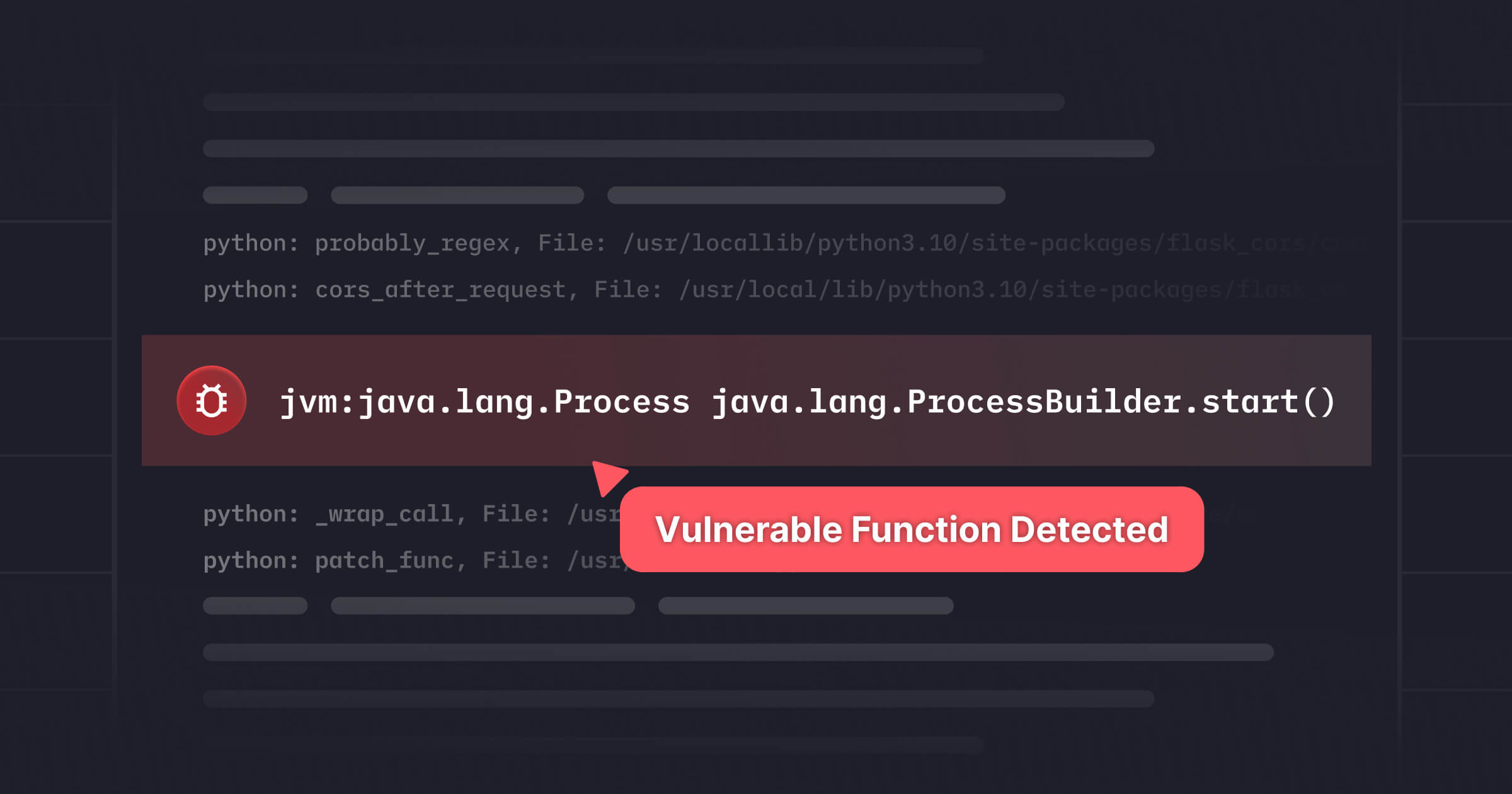
Function Executed → Specific CVE-implicated functions observed on live call stacks
Forensic proof of exploitability
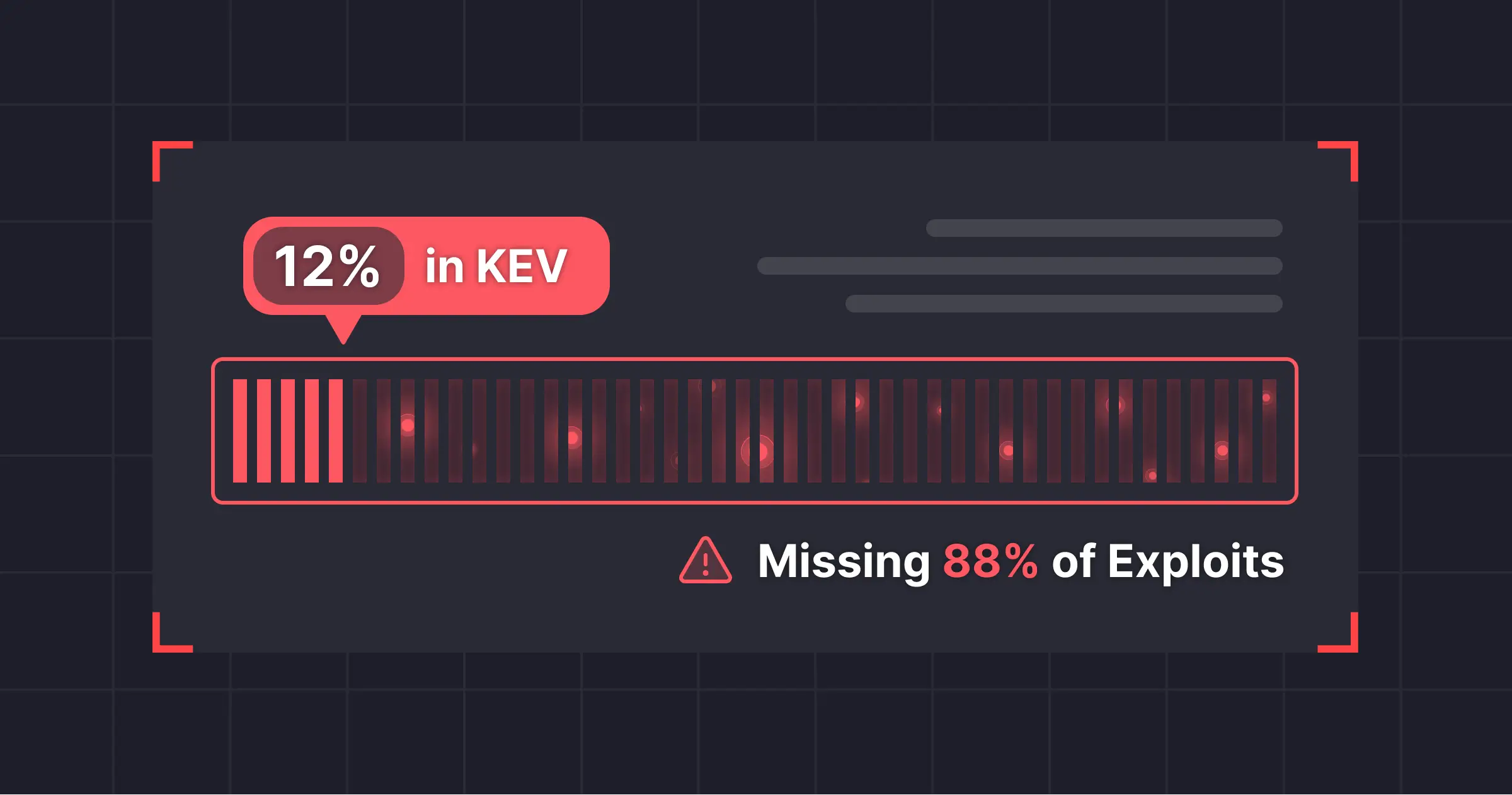
This final tier, when paired with confirmed internet reachability, represents the critical <1% of vulnerabilities that pose real risk. Function Executed status proves the vulnerable code path is active; reachability proves it can be triggered from outside your environment.
The difference is transformative. Instead of managing 5000 theoretical vulnerabilities, you focus on the 150 that are actually being executed - and among those, only 10 where the specific vulnerable functions run on production call stacks and the endpoints are internet-reachable.
Internet Reachability - confirm the vulnerable path is exposed
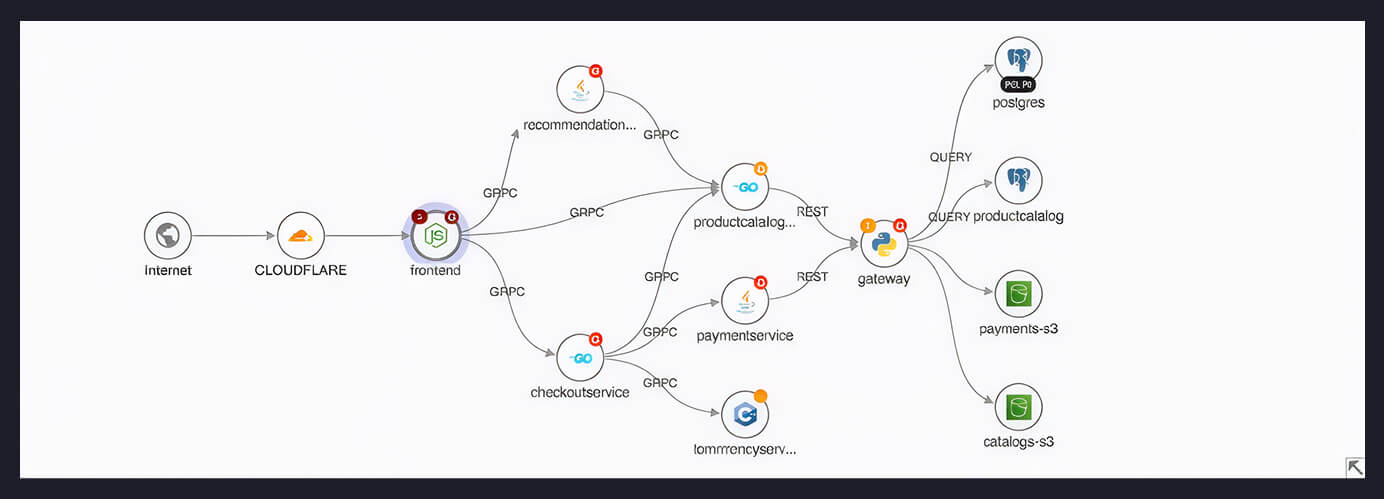
- Real-time traffic (Traces): Evidence of inbound requests reaching the service/route.
- Configuration analysis (Ingress & routes): Parse ingress objects and routing to model exposed endpoints.
- Active probing (hosts & domains): Validate external exposure and uncover misconfigurations or blind spots.
Technical Deep Dive: How Miggo Confirms Function-Level Exploitability
The precision comes from three systems working together to deliver unprecedented accuracy in vulnerability validation.
Our CVE Intelligence Engine goes far beyond standard vulnerability databases. We've built a proprietary knowledge base that maps CVEs to their exact vulnerable functions through:
- Analysis of official vulnerability advisories and security bulletins
- Examination of git commits, patch diffs, and security researcher reports
- LLM-powered extraction of function names from vulnerability descriptions
- Continuous validation against new disclosure patterns
This creates a dynamic knowledge graph that tells us precisely which functions are implicated in real-world CVEs - even when official advisories don't specify them.
The Production Runtime Profiling system uses eBPF-based instrumentation to capture complete call stacks from running applications with minimal overhead. Unlike traditional profilers focused on performance, our system is designed specifically for security validation:
- Continuous sampling for production safety (<1% overhead)
- Multi-language support
- Complete call stack capture
- Zero application code modification required
The Precision Matching Engine cross-references every observed stack frame against our vulnerability knowledge base.
Real-World Impact: Zero-Day Response in Action
Traditional Scenario: The Log4Shell Scramble
When CVE-2021-44228 affects a popular logging library, the familiar panic begins:
- Scanner alerts: "You have 847 applications using vulnerable log4j version"
- Security team: "Which ones are actually at risk?"
- Developer pushback: "How do I know if this affects my code?"
- Resolution timeline: Days to weeks of investigation and emergency patching
Teams scramble to assess impact while developers ask reasonable questions: "Can't we just disable the vulnerable feature? Which applications are actually calling this code?" These conversations burn precious hours during the critical remediation window.
Automated CVE Impact Assessment
Immediate Processing:
- CVE intelligence engine extracts vulnerable functions and updates knowledge base
- Reachability model updated: Parse ingress/routes, re-run targeted probes, and correlate with recent traces to confirm external exposure
- Historical runtime data is automatically re-analyzed against new threat intelligence
- Applications are instantly categorized by actual risk level
Precise Risk Classification:
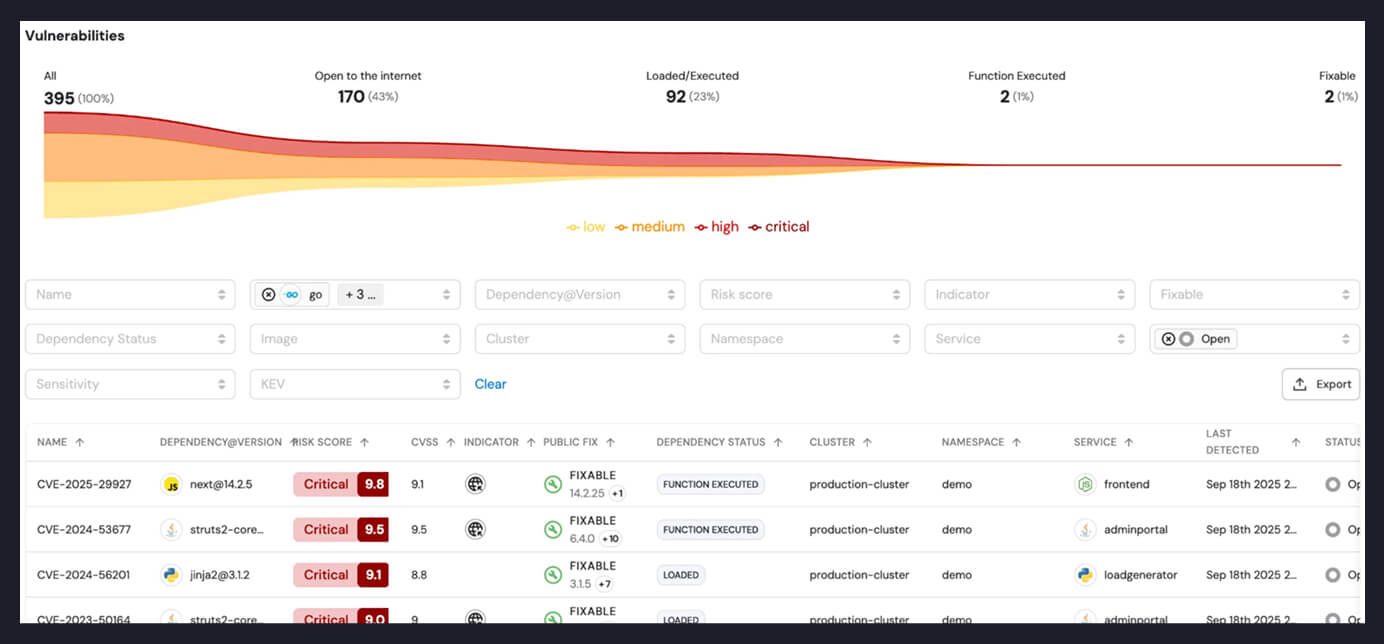
- Static Only (142 apps): Vulnerable package present but never loaded
- Loaded Only (89 apps): Package loaded but functions never called
- Executed Only (27 apps): Vulnerable functions observed
- Vulnerable Function Executed + Internet-Reachable (3 apps): CRITICAL - vulnerable functions actively used and exposed
Instant Developer Notification:
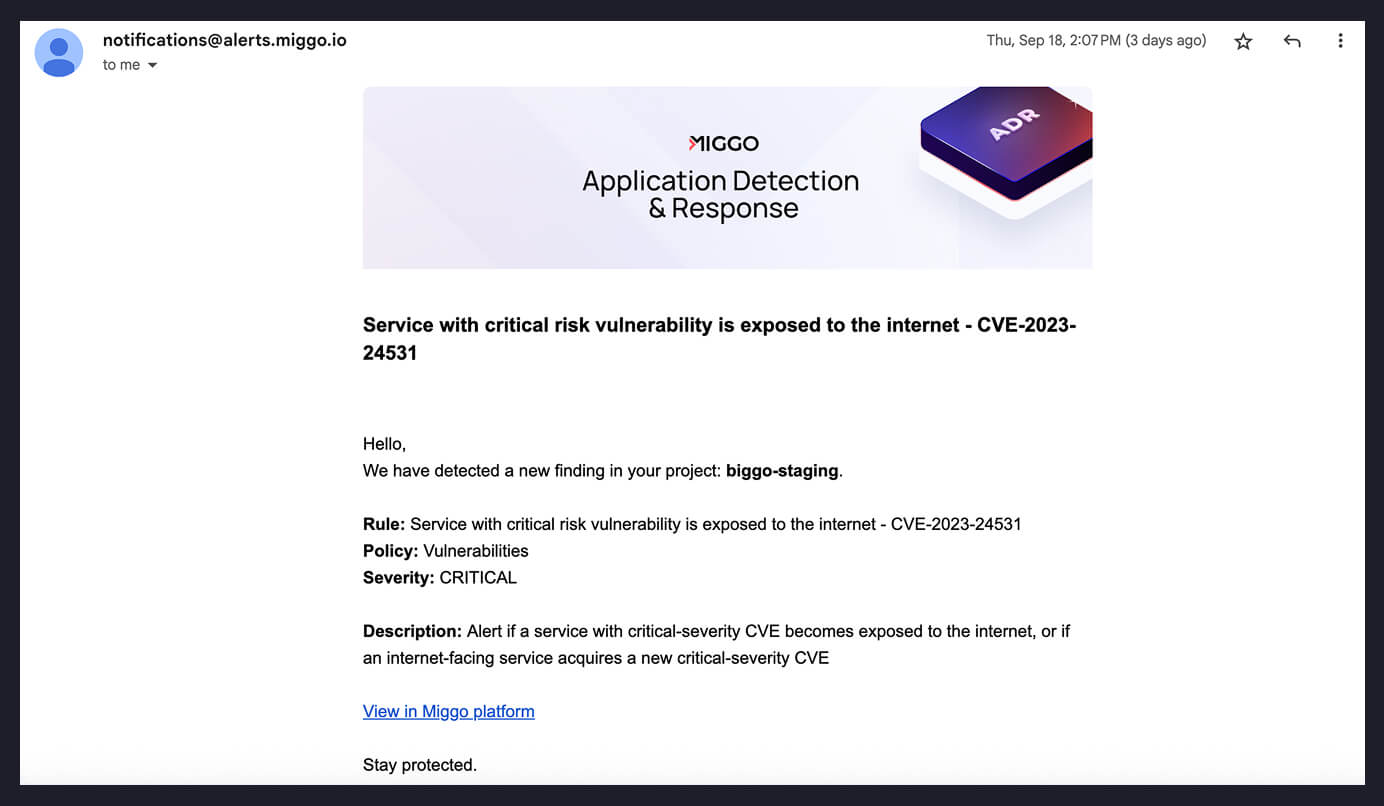
The Result: Security teams immediately know which 3 out of 234 applications require emergency patching, with forensic evidence showing how the vulnerability is triggered and that the services are internet-reachable. No guesswork, no developer arguments, no wasted effort on theoretical risks.
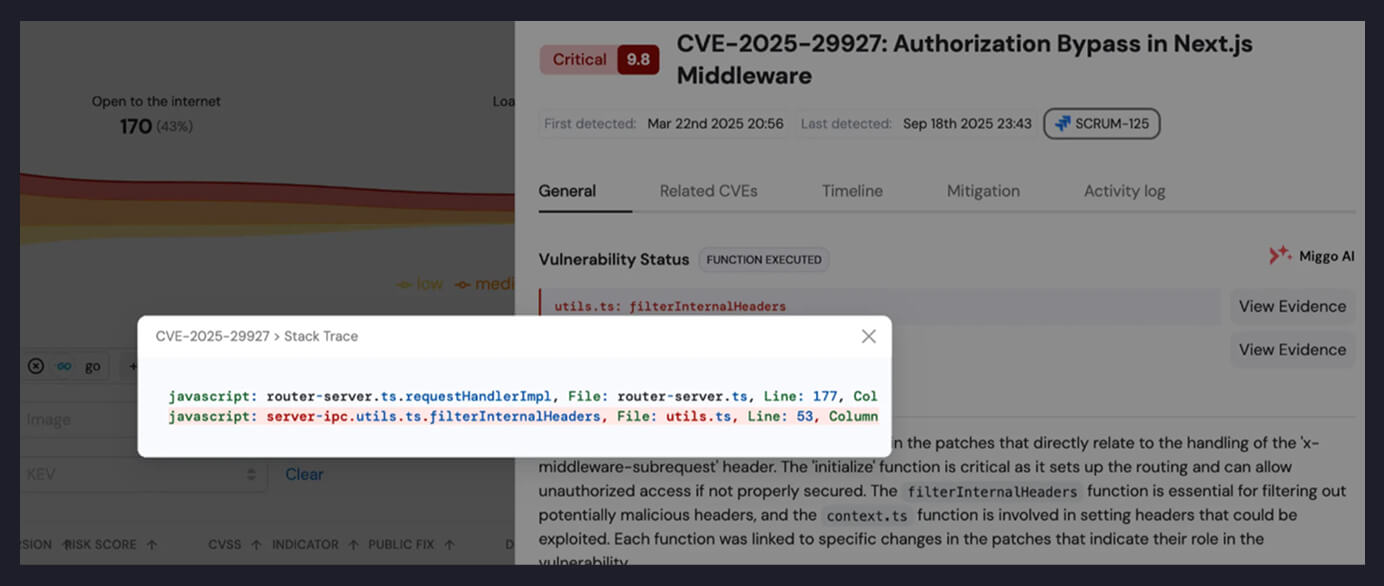
The evidence is unambiguous - timestamped stack traces showing the vulnerable function call in the context of real user requests. Developers can see exactly which code paths trigger the vulnerability, making remediation straightforward and justifiable.
The Business Impact: Precision Replaces Guesswork
For Security Teams: Reduce vulnerability backlogs by 95% while actually improving security posture by focusing only on genuine risks. Developer friction disappears when every alert comes with forensic evidence of exploitability.
For Development Teams: Alert fatigue ends when you receive only actionable vulnerabilities backed by production evidence. Remediation becomes straightforward because you can see exactly which code paths trigger vulnerabilities.
For Leadership: Quantify cyber risk with production-validated data instead of theoretical vulnerability counts. Board reporting transforms from defensive explanations to confident presentations of measurable risk reduction.
Stop Reacting to Theoretical Risk. Start Responding to Proven Threats.
The era of "spray and pray" vulnerability management is ending. Security teams need precision - the ability to identify and respond to the small percentage of vulnerabilities that pose real risk in their specific environment.
Miggo delivers that precision through function-level execution proof, transforming vulnerability management from a reactive burden into a strategic advantage. When you know exactly which vulnerabilities are exploitable and have forensic evidence to prove it, security becomes a competitive differentiator rather than a necessary evil.
Ready to transform your vulnerability management from overwhelming to strategic?
Request a demo and see how Miggo identifies the 1% of vulnerabilities that actually matter - with evidence your developers will trust and act on.