Today, we’re drawing attention to one of the most significant shocks to the JavaScript ecosystem in months: a massive supply-chain compromise hitting npm's most-used packages. For those that rely on packages like debug or chalk, what’s at stake isn’t just code, it’s the integrity of their crypto wallet.
The Background
On September 8, 2025, Aikido’s intel system flagged 18 heavily downloaded packages, including chalk, debug, ansi-styles, supports-color, and more.
Attackers injected obfuscated JavaScript into these packages. The payload was purpose-built to hijack browser-based crypto operations: it silently intercepted wallet interactions via window.ethereum, mutated transaction destinations, and redirected funds to attacker-controlled addresses, all under the guise of normal user interface behavior (aikido.dev).
This attack was unprecedented in its scale, affecting an estimated 2.6 billion weekly downloads and exposing countless applications to risk.
How It Happened: A Classic Phishing Play
The attacker's method:
- A phishing email disguised as npm support lured a maintainer into updating their Two-Factor Authentication settings.
- Under the guise of security urgency, the attacker gained control of npm account credentials and injected malware into legitimate package releases.
- The compromised packages automatically flowed into CI/CD pipelines, build tools, and countless downstream projects, even those that never directly depended on the affected ones.
Massive infection surface: These packages’ ubiquity means the malicious code likely slipped into countless projects—many indirectly—via transitive dependency chains.
Crypto-specific payload: While BleepingComputer didn’t detail the payload, npm’s Wikipedia summary notes the malware intercepted browser-based crypto transactions (e.g., window.ethereum) to siphon funds Wikipedia.
Deep Dive into the Threats & Why It Matters
- Unprecedented reach: With billions of weekly downloads, even indirect dependencies are now vectors for execution of malicious code.
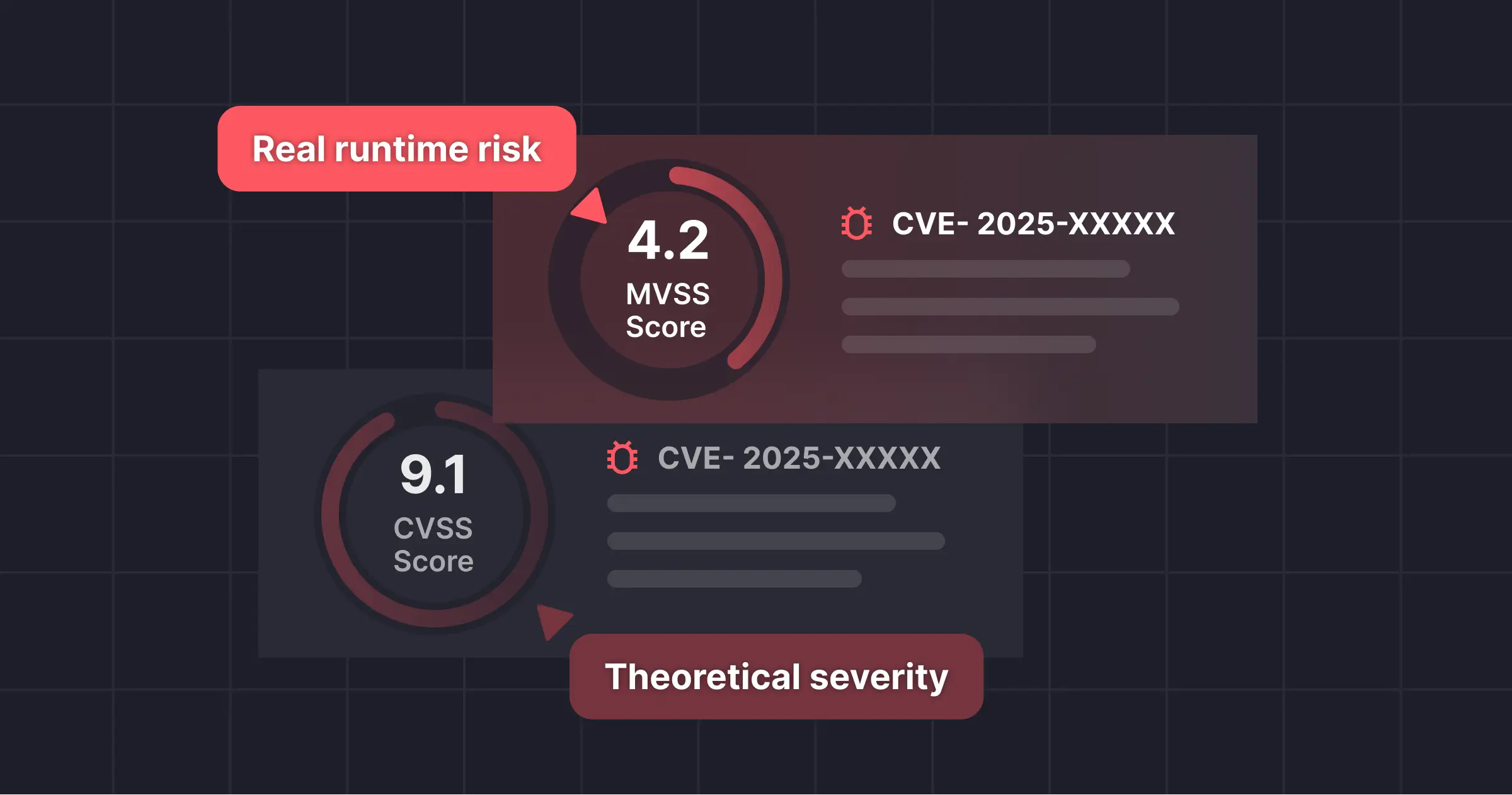
- Execution-time risk: Static scanning can't detect code that only triggers in runtime—this malware lurks until wallet APIs are invoked.
- Crypto under siege: Wallets and web3 users in affected apps are at immediate risk of silent fund redirection.
The packages hijacked so far (collectively have over 2.6 billion downloads every week - more here):
- backslash
- chalk-template
- supports-hyperlinks
- has-ansi
- simple-swizzle
- color-string
- error-ex
- color-name
- is-arrayish
- slice-ansi
- color-convert
- wrap-ansi
- ansi-regex
- supports-color
- strip-ansi
- chalk
- debug
- ansi-styles
How Miggo Checks Dependencies for Vulnerabilities
The Miggo Security platform is built to shift your security posture from reactive to proactive, ensuring you have visibility into your application's security from the start.
Here’s how our customers could check whether their systems are affected by the recent NPM/Chalk supply chain attack.
Miggo provides:
- Version filtering: We can see all impacted versions across environments but zoom in on one specific release to investigate further.
- Context-aware visibility: The dependency is displayed within the context of where it runs—helping teams assess real risk exposure.
- Execution status matters: In this case, the dependency shows as Executed, which raises the alarm. A vulnerability in a package that never runs is one thing; executed code is far more dangerous, especially when the exploit is designed to hijack runtime wallet interactions.
With Miggo, customers can integrate security seamlessly into the development process, ensuring that every piece of code, from their own to every single dependency, is trusted and secure. Miggo sends alerts when we find a vulnerable package being executed on a service – that is running all of a sudden – and the customer can then update the package to a secure version.
Final Thoughts
The September 2025 npm breach underscores a harsh truth: no package is too insignificant to ignore—and no install process is too trivial to trust by default.
That’s why Miggo focuses not just on what’s in your code, but on what your code does when it runs. Because in modern supply-chain warfare, runtime visibility and protection are your strongest shield.
If you are worried about a potential threat in your application environment or want to learn more, book time with our security experts.