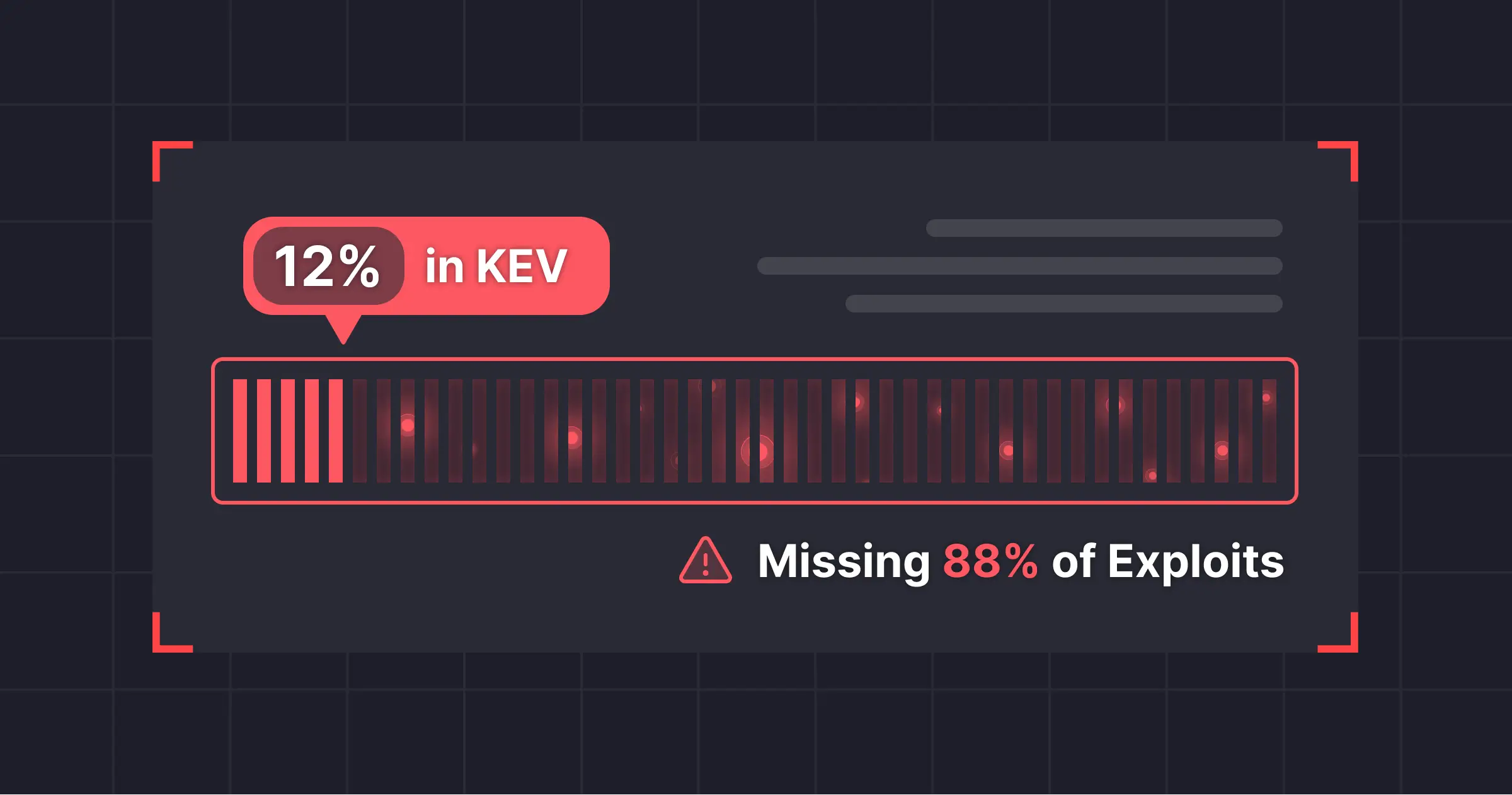
Cyber attacks continue to rise industry-wide, with application-level threats being a leading cause. Legacy tools were designed to focus on fragments of the application - whether it’s static code, configuration files, or just network traffic. This has left teams lacking the complete behavioral context needed to differentiate between normal behavior and active attacks to stay ahead of the growing threats.
To combat threats, shadow applications, and to facilitate active defenses when necessary, we kicked off a transformative journey building an Application Detection and Response (ADR) Platform that captures actionable insights at runtime. In this article, we’ll share how we built the Miggo ADR Platform, solve key challenges, and set a new standard for application security.
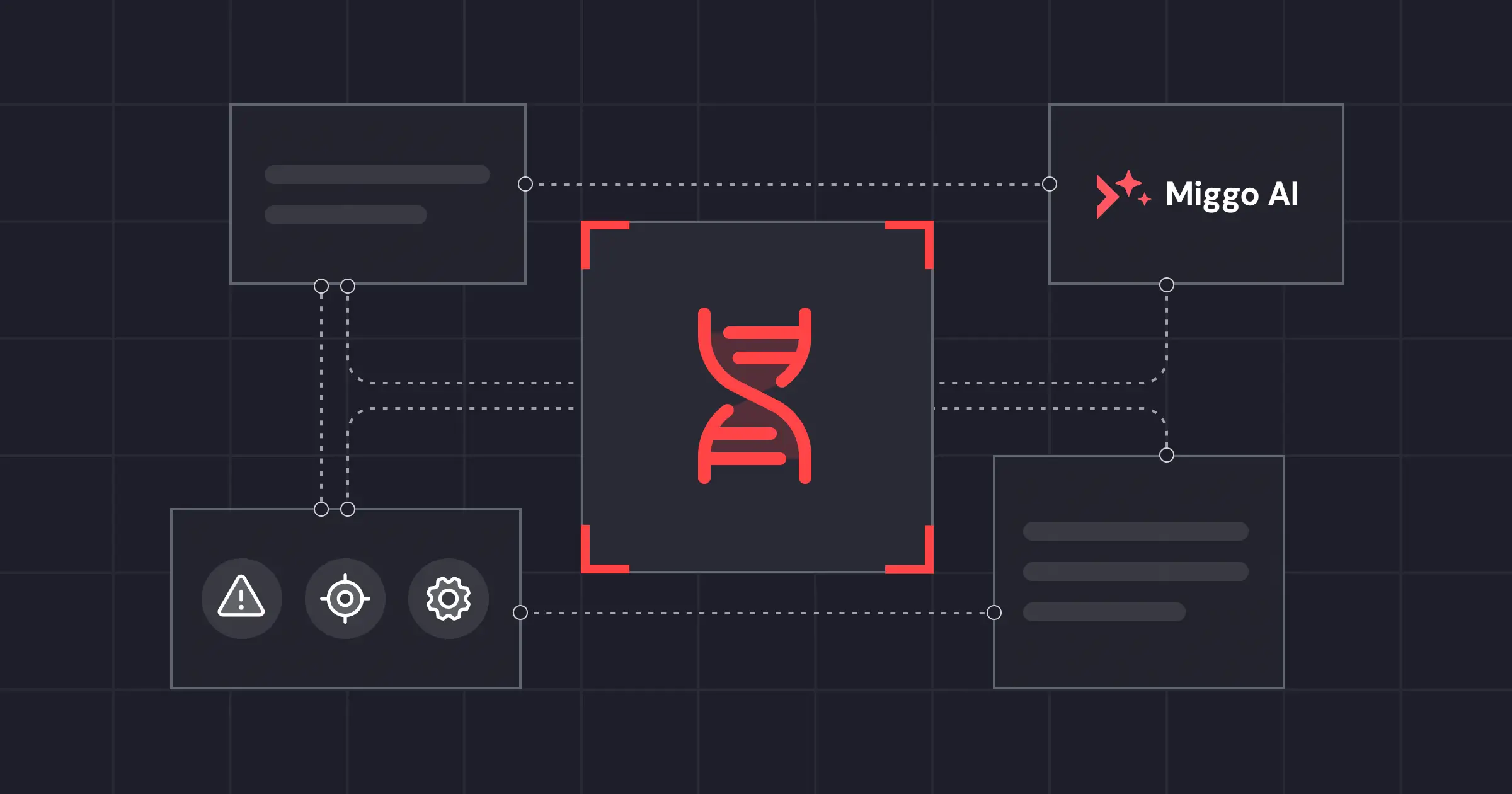
Miggo’s Runtime Application DNA
At Miggo, we assembled a set of thought leaders within the company to define the ADR standard and build a visionary solution. We've developed an approach to application security that builds on a fundamental insight: Understanding how an application behaves at runtime. At the heart of our ADR lies a robust architecture that translates to several key components that empower seamless communication and functionality extension.
A Runtime Powered Application Model
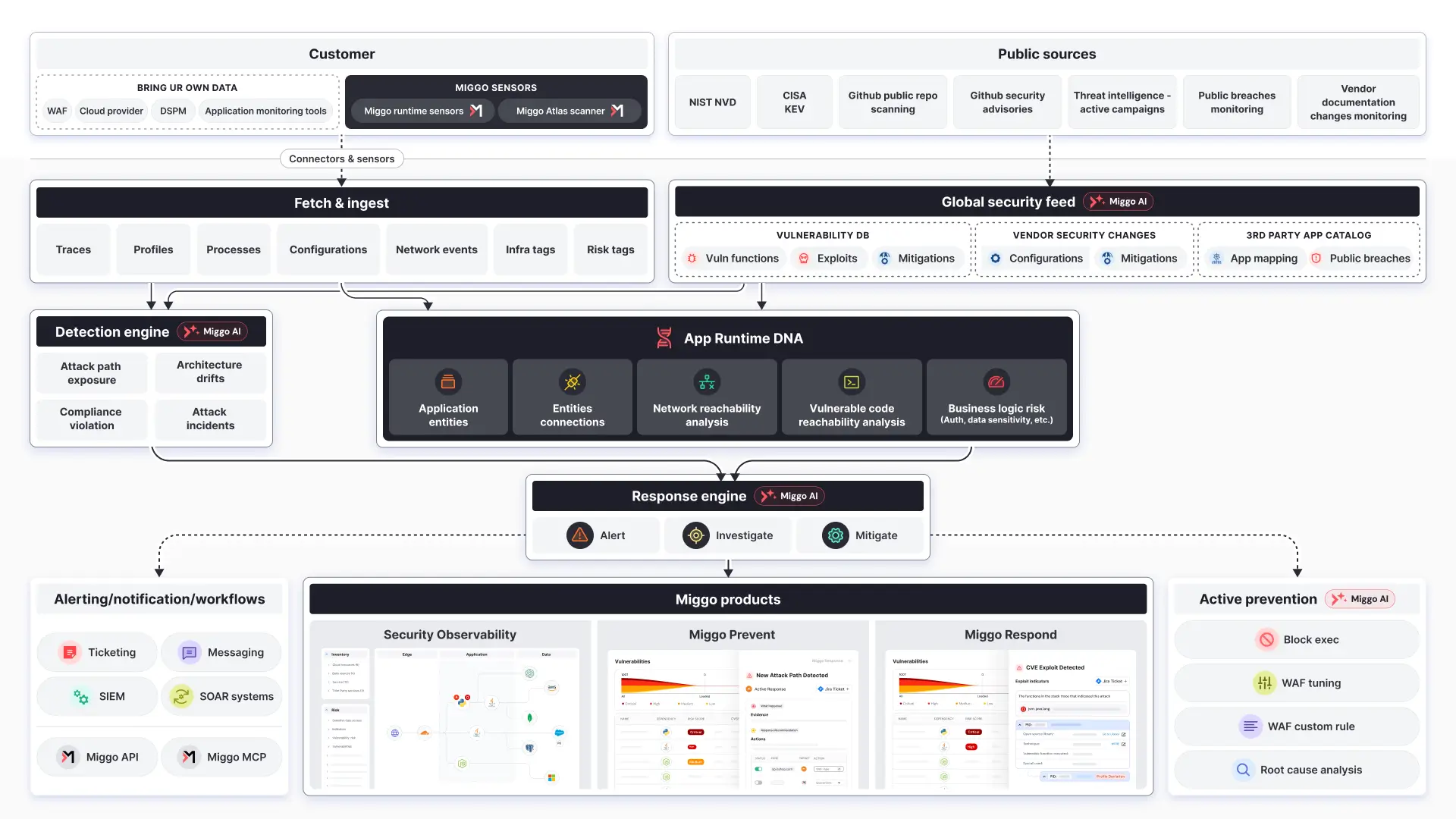
Our Application Runtime DNA creates a comprehensive blueprint of an environments running applications, capturing multiple dimensions of runtime data in a security-aware model. It’s built using four key elements:
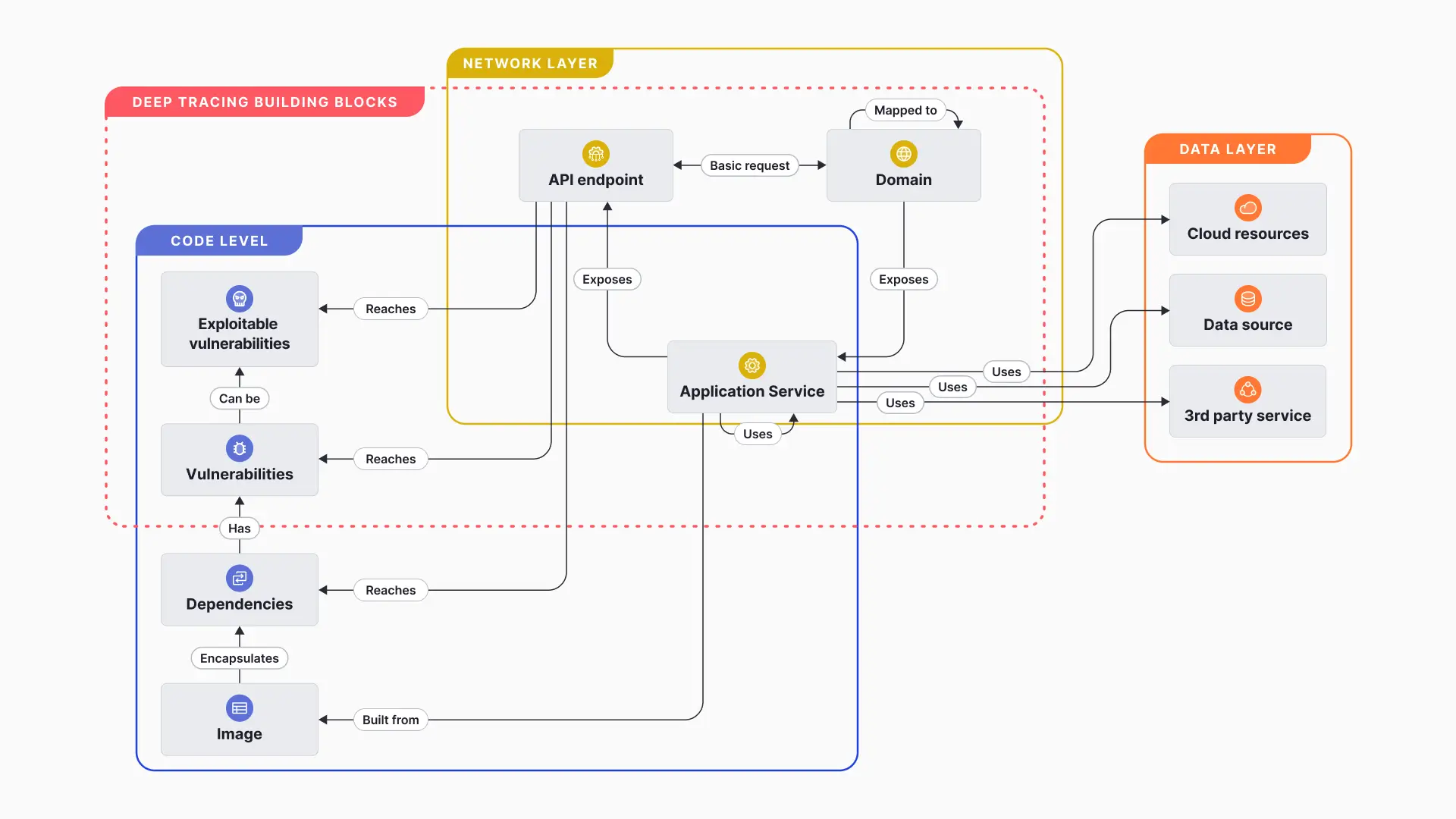
- DeepTracing™: We analyze and correlate distributed traces and runtime profiles to reveal active code execution paths, API interactions, and data flows between services. This enables visibility into how applications behave in real-world conditions.
- Application Entity Model: A complete inventory of your application landscape to map all critical elements in your application environment. This includes but is not limited to application services, API endpoints, domains, data sources, cloud resources, third-party services, container images, dependencies, and vulnerabilities.
- Application Entity Mapping: Accurately identify how components interact and are connected by leveraging a dynamic graph. This reveals which services access sensitive data, how dependencies are structured, and potential attack paths.
- Application Evolution Monitoring: Track how applications evolve, establishing behavioral baselines to detect deviations that indicate active attacks or departures from best practices.
Having these four layers creates a solid foundation to make the data truly meaningful and actionable.
Application Security Requires Contextual Enrichment
Another approach that we’ve invested in at Miggo is enhancing runtime data and combining it with critical context from multiple sources; contextual enrichment. This ensures we can provide users with a deeper level of understanding for effective security and performance optimization. To achieve this we’ve merged the following technologies into a single solution:
- Network Reachability: Analyze an attacker's potential path to applications by examining live traffic through distributed traces, infrastructure configurations for ingress control, and actively testing discovered public entry points.
- Code-Level Reachability: Monitor executed code to identify exploitable vulnerabilities by mapping API calls to function execution patterns, analyzing functions against our proprietary vulnerability database, and assessing internet-to-code flows that indicate potential attack vectors.
- Business Impact: Incorporate data sensitivity assessments, encryption patterns in service communications, authentication analysis for API endpoints, business line attribution, and engineering team ownership to align security with business priorities.
- Infrastructure Insights: Integrate both Kubernetes clusters and cloud provider infrastructure data to complete the full picture of an application's operating environment.
- Environmental Context: Bring unique context into the model, ensuring Miggo’s solution adapts to your specific needs and priorities.
From Visibility to Actionable Security
For most teams, their security tools give them the alert required to know something has happened but then leaves their hands tied when it comes to how it happened and how to respond. Miggo transforms this and pivots teams from knowing about a threat to taking relevant action. We do this by enabling teams with several key options:
- Attack Path Analysis: By understanding how components actually interact in runtime, we can identify real exploitable paths that attackers could use to reach sensitive assets, not just theoretical ones.
- Active Detection: Our Detection Engine uses this rich context to accurately distinguish between normal behavior and actual attacks, dramatically reducing false positives.
- Contextual Response: When threats are detected, our Response Engine has the full application context needed to understand impact and guide precise mitigation, from instant one-click compensating control mitigation, to tailored and contextual recommendations.
- Hybrid Deployment Architecture: Our users can get started with a hybrid deployment that combines agentless data collection with lightweight modern sensors. This approach gives teams: the non-intrusive nature of agentless monitoring for broad coverage, plus the deep visibility of purpose-built lightweight sensors where needed. Unlike traditional tools that require heavy agents with significant performance impacts, Miggo's sensors are designed for modern distributed systems with minimal overhead.
Conclusion
While other solutions claim to provide runtime protection or cloud-native security, they typically focus on isolated aspects, either code-level instrumentation or cloud configurations. Miggo's approach is fundamentally different, creating a unified view that bridges application logic, infrastructure, and security contexts.
Miggo is the only ADR that focuses on understanding applications as they actually run in production, not just analyzing static code or infrastructure configurations in isolation. By building and continuously updating the Application Runtime DNA, we enable security teams to move at the speed of development while providing the deep understanding needed to protect against sophisticated threats in the AI era. This isn't just incremental improvement, it's a new foundation for application security that matches the reality of modern distributed systems.