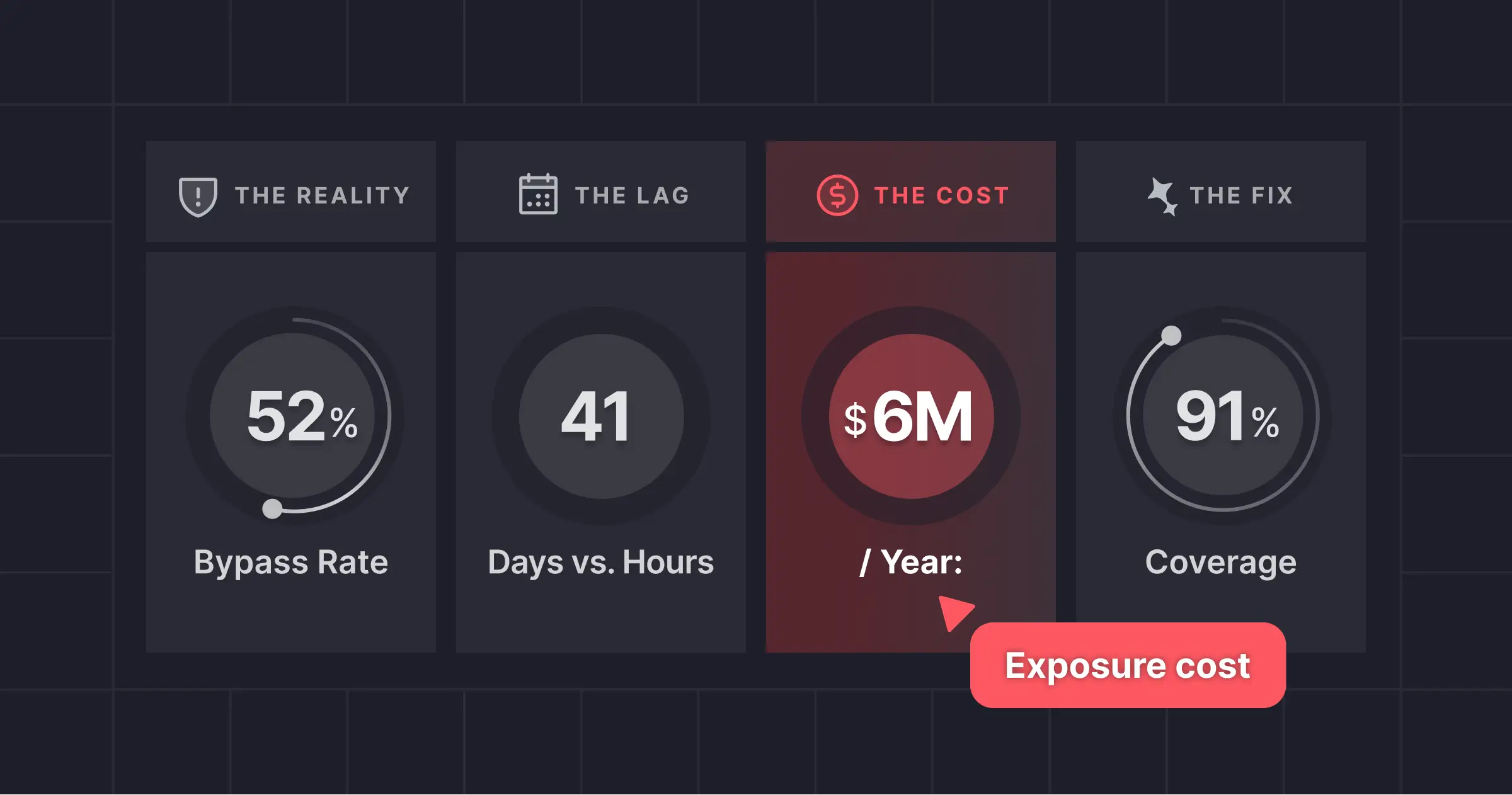
In today's dynamic application landscape, threats are no longer hiding in the source code or in third-party libraries. They're alive, active, and operating within the runtime behavior of applications, making them invisible to traditional security tools. Static scans and pre-deployment checks are crucial, but what happens when your application is live, interacting with users, services, and data? This is the unseen battlefield where sophisticated attacks and subtle posture vulnerabilities form.
At Miggo, we’ve designed our solution to spotlight this critical space. As an Application Detection and Response (ADR) platform, we decode an application through runtime profiles and trace data, creating what we call your AppDNA. This isn't just about finding vulnerabilities before deployment; it's about detecting active attacks and identifying exploitable weaknesses as they manifest in real-time.
Below we dive into how Miggo transforms raw, complex runtime data into clear, actionable security intelligence, empowering any team to see and block active threats.
Why Runtime Insights are a Game-Changer in the Age of AI
Runtime security is paving the path for modern active attack path control. Legacy security tools have often treated security like a blueprint and as a parts list for a car. They’ll tell you if the design is sound, what the design is, and if the components are known to be safe. But they don't tell you how the car is actually being driven, if someone is trying to hotwire it, or if a critical system is showing signs of stress under load.
That's where runtime insights from application profiling and trace data come in. This data provides a continuous, live feed of your application's behavior:
- OS Interaction Monitoring: Capture the moments when your application interacts with the operating system to perform significant actions, like starting new processes, creating a network connection, or accessing the file system. It’s like listening to the OS's whispers about what your application is really up to.
- Application Profiles & Traces: Offer a window into the application's internal execution paths, showing which functions are being called, how frequently, and in what sequence. This is akin to mapping the application's internal highways and byways, watching the traffic flow.
This "in-action" perspective is vital because many modern attacks and vulnerabilities only become apparent when the application is live. They exploit the dynamic interplay of code, data, and environment – something static analysis alone cannot fully predict or observe.
Decoding Application Behavior for Unmatched Clarity with Miggo
Miggo’s ADR platform doesn't just collect profiles and traces; it translates them into high-fidelity security signals:
- Unmasking Rogue Operations through Application <-> Operating System Interaction Monitoring: When an application unexpectedly spawns a shell (like
/bin/bash), a network utility (likencorcurl), or any process not typically expected during normal operations. Miggo instantly detects and flags this unusual behavior by monitoring the application and operating system interactions.. This is often the smoking gun for successful command injection or remote code execution. We also scrutinize command arguments and environment variables, sniffing out attempts to leak sensitive data like API keys or passwords passed carelessly to child processes. - Tracing Malice with Application Profiles & Traces: These detailed execution maps allow Miggo to spot the subtle footprints of an attack in progress. We identify:
- Calls to dangerous APIs: Think
eval()in Python,Runtime.exec()in Java, orchild_process.exec()in Node.js being invoked in suspicious contexts. - Exploitable sequences: Miggo detects situations where legitimate code fragments are combined in unintended ways during deserialization ("gadget chains"), enabling attackers to execute malicious actions.
- Anomalous network behavior: Is your application suddenly trying to reach internal IP addresses it never contacted before? Or making outbound calls to known malicious domains? This could be SSRF in action.
- Suspicious file interactions: Attempts to access sensitive system files (
/etc/passwd), including remote files (RFI), or traverse directories (../../) are highlighted. - Weak cryptographic practices: Miggo detects when your application actively uses outdated or insecure encryption algorithms, such as MD5 or DES, potentially exposing your data to risk.
- Vulnerable libraries in action: It's one thing to know a vulnerable library exists in your manifest; Miggo shows you if that vulnerable code is actually being executed at runtime, helping prioritize what truly matters.
- Calls to dangerous APIs: Think
And crucially, Miggo enriches all this data with context. Knowing which pod, container, and command initiated an action allows for precise baselining and drastically reduces the noise, ensuring that alerts are relevant and actionable.

The Common Attacks Miggo Detects
Miggo’s runtime analysis brings clarity to some of today's most pervasive application attacks:
- Deserialization of Untrusted Data (CWE-502): The Trojan Horse
- The Threat: Attackers craft malicious data that, when deserialized by your application (e.g., Java's
ObjectInputStream.readObject(), Python'spickle.load()), executes arbitrary code, often leading to complete system compromise. - Miggo's Edge: application profiles show the deserialization function call. Then, in a deadly one-two punch, the operating system profiling captures the spawned shell or malicious command if the attack succeeds. Miggo connects these dots, providing irrefutable evidence of the exploit chain.
- The Threat: Attackers craft malicious data that, when deserialized by your application (e.g., Java's
- OS Command Injection (CWE-78): Hijacking the System
- The Threat: User-supplied input gets improperly embedded into a system command, allowing attackers to run their own commands on your server.
- Miggo's Edge: The Connection between application profiles and the operating system behavior is very helpful. We see your application (e.g., a Python script using
os.systemor a Go program misusingos/exec) suddenly birth a suspicious process likesh -c "attacker_command". Application profiling can also highlight the vulnerable code path where user input meets command execution.
- Server-Side Request Forgery (SSRF) (CWE-918): The Internal Spy
- The Threat: Attackers trick your server into making requests to internal, typically unreachable systems or sensitive cloud metadata endpoints (e.g., AWS IMDS
169.254.169.254). By forcing the server to query these special addresses, attackers can retrieve temporary security credentials and other secrets stored within the cloud environment. These stolen credentials grant them the same level of access as the compromised server, enabling them to move laterally and access other cloud resources. - Miggo's Edge: Appliaction profiles reveal calls to HTTP client libraries (in any language – Java, Python, Node.js, Go, Ruby, .NET, C++, and more ) with target URLs pointing to internal IPs or the metadata service. We baseline normal outbound connections, making anomalous requests stand out starkly.
Having knowledge of the library executing the request and the parameters also helps us reduce the false positives in the SSRF case.
- The Threat: Attackers trick your server into making requests to internal, typically unreachable systems or sensitive cloud metadata endpoints (e.g., AWS IMDS
- Path Traversal & File Inclusion (LFI/RFI) (CWE-22, CWE-98): Unwanted Guests
- The Threat: Attackers manipulate file path inputs to read sensitive files from your server (LFI) or include and execute remote malicious files (RFI).
- Miggo's Edge: Application profiles show file access functions (like Python's
open(), Java'sFileInputStream, Node.js'sfs.readFile, Go'sos.Open, or Ruby'sFile.open) being called with suspicious paths containing../sequences or URLs to external sites.
Identifying Latent Posture Flaws Before They're Exploited
Miggo’s ADR capabilities extend beyond just detecting active attacks. The same deep runtime visibility allows us to proactively identify security posture weaknesses that could be exploited tomorrow:
- Leaky Secrets: Application interactions with the underlying operating system can reveal API keys, database credentials, or other secrets inadvertently passed as command-line arguments or exposed in environment variables of spawned processes. Miggo helps you plug these leaks before attackers find them.
- Weak Cryptography: Application profiles show if your application is actively using outdated or weak cryptographic algorithms (e.g., MD5, SHA1, DES) or insecure modes of operation. This allows you to modernize your crypto before it’s cracked.
- Dormant Libraries: Software Composition Analysis (SCA) tells you about vulnerable libraries in your dependencies. Miggo’s runtime analysis tells you if those vulnerable libraries, and specifically the vulnerable functions within them, are actually being executed in your live environment. This is critical for prioritizing patching efforts on what poses a tangible risk. Besides telling you the vulnerable functions are executed, Miggo has the context on the service, so it also tells you that the vulnerability exists on an internet-exposed service, or an internet-exposed-by-proxy service, which helps prioritize even more.
- Risky Configurations: Is a production service running with debug flags enabled? Is an application unexpectedly running with root privileges? Miggo spots these insecure configurations by analyzing process attributes and execution paths.
From Data Overload to Actionable Defense
Teams need to be able to transform rich runtime insights into clear, prioritized, and actionable intelligence for your security teams. Miggo’s ADR leverages sophisticated baselining of normal application behavior and advanced anomaly detection techniques to minimize false positives and ensure that your team focuses on genuine threats, whether they’re disclosed or undisclosed. This means immediate threat mitigation and the ability to proactively harden your applications against the attacks of tomorrow.
Securing Your Future with Runtime Insights and Miggo
In the evolving cybersecurity landscape, what you can't see can hurt you. Applications are no longer static fortresses but dynamic entities whose runtime behavior holds the key to their security.
Miggo provides the X-ray vision you need to penetrate the complexities of your live applications. By meticulously analyzing runtime profiles and trace data, we empower you to detect active attacks in real-time and uncover hidden posture vulnerabilities before they become tomorrow's headlines.
Don't let your application's runtime be a blind spot. Illuminate it. Secure it. With Miggo.
Ready to see what’s truly happening inside your applications? Book time with an ADR expert now.



.webp)