Vulnerabilities Aren't Just Flaws — They're Attack Paths
Every vulnerability represents a potential attack path into your applications. But here's the critical question: which of these paths are actually traversable by attackers in when your code is in production?
Traditional vulnerability management treats each CVE as an isolated security flaw to be patched. This approach misses a fundamental reality: attackers don't exploit vulnerabilities in isolation. They exploit attack paths through running applications. A vulnerability only becomes dangerous when it forms part of an active attack path that an adversary can actually exploit.
The difference between a theoretical vulnerability and an exploitable attack path comes down to one thing: runtime context.
Why Runtime Context Is Everything
Attackers operate in runtime environments, not in static code repositories. They exploit vulnerabilities that are actively loaded, reachable through network interfaces, and connected to valuable resources. This is why runtime context fundamentally changes vulnerability risk assessment.
Consider two scenarios:
Scenario A: A critical vulnerability (CVSS 9.8) exists in a logging library that's bundled with your application but never actually executed in production. From an attacker's perspective, this isn't an attack path, but a dead end.
Scenario B: A moderate vulnerability (CVSS 7.4) exists in an authentication function that processes every user request, has network exposure, and handles sensitive tokens. This represents a live attack path that attackers can actively exploit.
Static analysis tools and traditional CVSS scoring would prioritize Scenario A. Runtime-aware security focuses on Scenario B — because that's where real attacks happen.
Introducing the Miggo Risk Score: Attack Path Prioritization Through Runtime Intelligence
The Miggo Risk Score changes how security teams understand and prioritize attack paths by combining global threat intelligence with live runtime context. Instead of treating vulnerabilities as isolated incidents, it evaluates them as potential components of exploitable attack paths.
This approach answers the question every security team should be asking: "Which vulnerabilities form active attack paths that adversaries can actually exploit in my runtime environment?"
Two Signals, One Attack Path Assessment
The Miggo Risk Score creates a comprehensive 0-10 risk rating by combining:
1. Public Threat Indicators
Global intelligence about vulnerability exploitation patterns:
- CVSS scores for baseline severity assessment
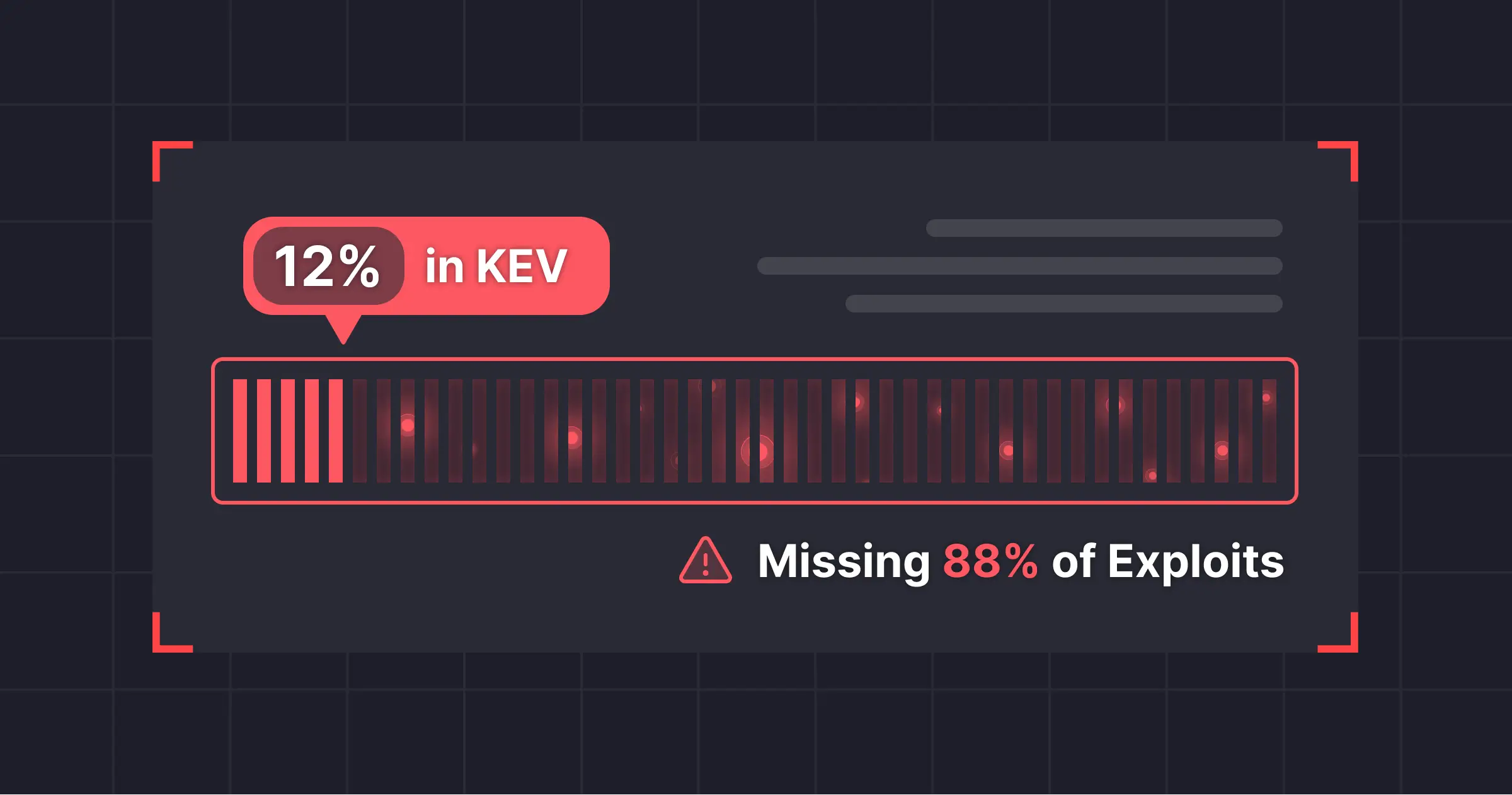
- EPSS predictions for exploitation likelihood in the next 30 days
- KEV catalog entries for confirmed wild exploitation
2. Runtime Context Intelligence
This is where Miggo's runtime-first approach becomes critical. Miggo’s distributed telemetry collectors operate directly in your production environment, gathering real-time signals about how vulnerabilities behave in actual attack scenarios:
- Execution Context: Is the vulnerable code path actively executed during runtime operations?
- Network Reachability: Can attackers access the vulnerable component through network interfaces?
- Authentication Bypass: Are there unauthenticated paths to the vulnerable functionality?
- Privilege Escalation Potential: Does the vulnerability provide access to sensitive data or critical systems?
These signals map the actual attack surface that adversaries can exploit, rather than theoretical possibilities.

Runtime Intelligence in Action: Transforming Security Operations
Here's how runtime context transforms vulnerability management:
SecureTech's Transformation:
SecureTech's application security team previously managed 1,200+ monthly vulnerability alerts using traditional CVSS-based prioritization. They spent 60% of their remediation effort on high-scoring vulnerabilities that were often dormant in production, while missing active attack paths with lower static scores.
Runtime-Driven Results:
With Miggo's runtime intelligence, the team now identifies the 3% of vulnerabilities that form active attack paths in their environment. A recent example: they correctly deprioritized a CVSS 9.8 vulnerability in an unused code branch while immediately addressing a CVSS 7.4 in their payment processing flow — which was actively handling customer transactions and had direct network exposure.
Business Impact:
- Attack Surface Reduction: Focus remediation on actual attack paths rather than theoretical vulnerabilities
- Resource Optimization: Development teams fix vulnerabilities that matter in runtime
- Faster Threat Response: Clear attack path visibility enables rapid response to genuine risks
- Demonstrable Security ROI: Evidence-based prioritization shows clear security value to stakeholders
From Vulnerability Lists to Attack Path Intelligence
Traditional vulnerability scoring was designed for simpler applications in more predictable environments. Today's complex, distributed runtime environments demand an approach that understands how attackers actually operate: by exploiting paths through live, running applications.
The Miggo Risk Score represents a fundamental shift from static vulnerability assessment to dynamic attack path analysis. It moves beyond asking "How severe is this vulnerability?" to "Does this vulnerability create an exploitable attack path in my runtime environment?"
This is security that operates where attacks actually happen: in runtime.
Ready to focus on the attack paths that actually threaten your applications?
Discover how runtime intelligence transforms vulnerability management. Book a demo today and see attack path prioritization in action.
Learn more about Miggo's runtime security approach at miggo.io